Offensive Sysadmin Suite, aka Adversary Kit
The Offensive Sysadmin Suite provides a comprehensive set of tools presented in PowerShell and C#. This post dives into the functions of each.

The Offensive Sysadmin Suite provides a comprehensive set of tools presented in PowerShell and C#.
These tools were designed to uncover vulnerabilities and misconfigurations within active directory domains. Whether you're a red teamer aiming to expose vulnerabilities or a defender committed to fortifying your systems, they serve as an invaluable asset in navigating the complex landscape of active directory domains.
The table below provides an overview of each tool's functionality, while the subsequent subsections explain the step-by-step instructions for utilizing each tool.
| Name | Language | Description |
|---|---|---|
| DomainScrape | PS | Hunt for keywords in documents across domain shares. |
| Invoke-Ghost | PS | Only scrapes metadata from office documents from an entire directory, a stealthy way to grab usernames. |
| ScrapingKit | PS & C# | Scraping Kit comprises several tools for scraping services for keywords, useful for initial enumeration of Domain Controllers or if you have popped a user's desktop, their outlook client. |
| SharpCreds | C# | Automates the harvesting of domain user accounts / password stuffing/domain groups, which can be used from domain or nondomain joined hosts. |
| SharpShares | C# | Takes no input, executes, and gives you a list of shares the domain user can access. |
| SlinkyCat | PS | A collection of AD Audit functions for easy identification of misconfigurations within active directories, users, groups, permissions, and mishandling data within objects |
SharpCreds
SharpCred offers users the ability to authenticate with a domain, generate or load a list of usernames, and verify if a provided password matches any of the accounts. It also retrieves the domain groups associated with valid credentials and identifies high-privileged accounts. Additionally, the program allows enumeration of the domain password policy and provides an interactive menu for executing these operations.
SharpCreds Demonstration
SharpCred initiates by prompting the user to enter their domain credentials for authentication. It can be executed from both domain-joined and non-domain-joined machines. Upon successful authentication, the program enters a menu loop, providing the user with a selection of various options.
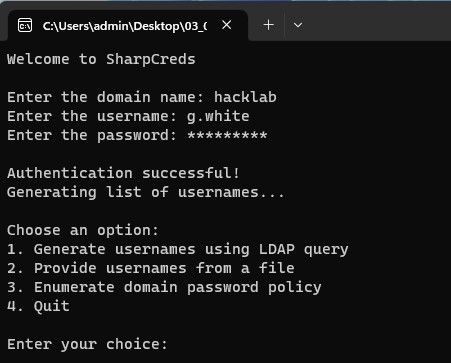
Option 1: Automatically generates a list of usernames by querying the LDAP directory of the specified domain.
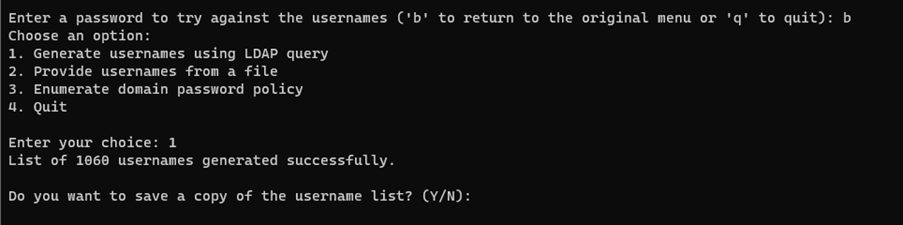
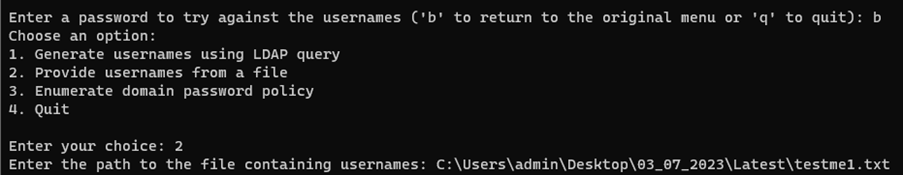
Option 2: Enables the user to provide a file containing usernames, which are subsequently loaded into a list.
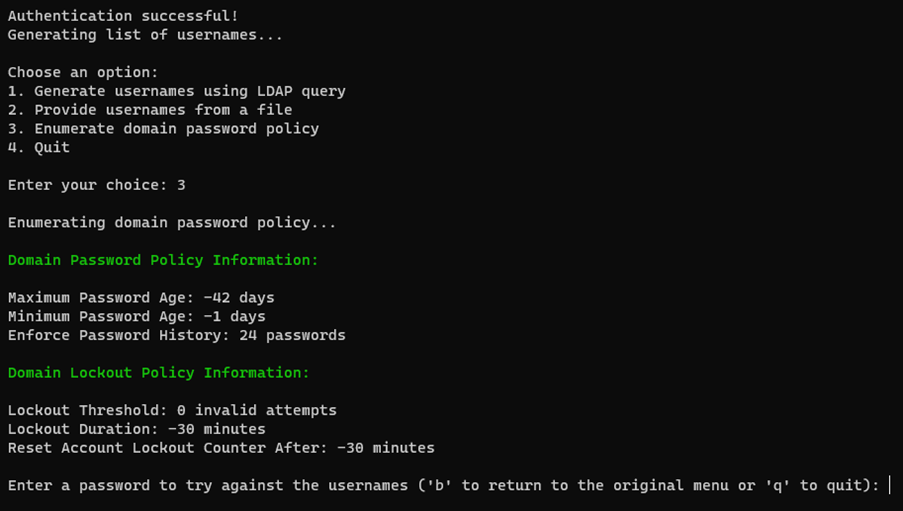
Option 3: Retrieves and displays the domain password policy by querying the domain.
Option 4: Closes the program.
After generating or loading a list of usernames, the program prompts the user to enter a password of their choice, such as Welcome123.

After pressing enter, the program iterates through the list of usernames, attempting to authenticate each one with the provided password. If authentication is successful, the program retrieves and displays the domain groups associated with the valid credentials. Additionally, the program checks for high privileged accounts by comparing the retrieved groups with a predefined list of privileged groups.
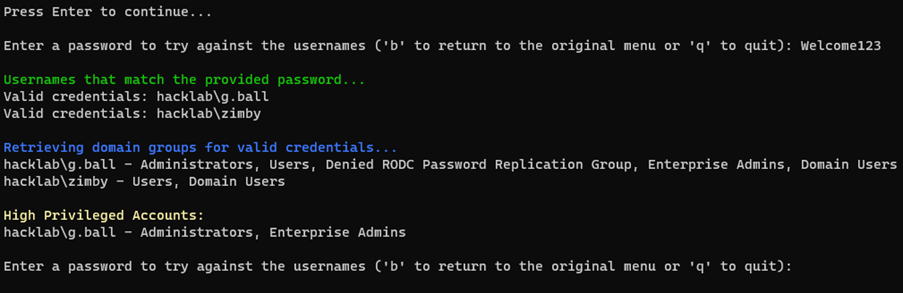
The program continues this loop until the user chooses to return to the original menu or quit. Overall, it combines authentication, LDAP querying, File Input/Output, and Active Directory operations to offer a comprehensive tool for username authentication, group retrieval, and password policy enumeration within a specified domain.
SharpCreds Detailed Overview
SharpCred initiates by prompting users to enter their domain credentials (username and password) for authentication. It utilizes the DirectoryEntry class from the System.DirectoryServices .NET namespace to establish a connection with the designated domain's directory. Bypassing the domain name, username, and password to the DirectoryEntry constructor, it attempts to access the NativeObject property of the DirectoryEntry instance. If the authentication process is successful, the program enters a menu loop, offering the user a selection of various options.
Option 1: Automated username harvester utilizes the DirectorySearcher class to perform an LDAP query on the directory. It defines a filter to retrieve user objects and specifically targets the sAMAccountName property. The program collects a set of SearchResult objects and extracts the sAMAccountName values from them, generating a comprehensive list of usernames.
Option 2: Manual username selection prompts the user to specify a file path. The program employs the File.ReadAllLines method to read the file's contents, treating each line as a separate username entry and adding it to the list.
Option 3: This option employs an additional instance of the DirectorySearcher class from the System.DirectoryServices namespace which is also from the .NET Framework. It executes a query on the domain object and retrieves properties pertaining to the domain password and account lockout policy.
After generating or loading the list of usernames, the program then prompts the user to input a chosen password. It then proceeds to iterate through each username in the list, utilizing the AuthenticateUser method to perform authentication. For each iteration, a new DirectoryEntry instance is created with the username and the provided password, attempting to access the NativeObject property. If the access is successful, the authentication is considered valid.
Upon valid authentication, the program retrieves the domain groups associated with the authenticated user. It leverages the PrincipalContext and UserPrincipal classes from the System.DirectoryServices.AccountManagement namespace to query the groups.
Finally, the program examines the retrieved groups by comparing them with a predefined list of privileged groups to identify high-privileged accounts. It establishes a dictionary to store the matched accounts along with their corresponding groups. In the end, the program displays any valid credentials that have matched, along with the associated domain groups and the high-privileged accounts found.
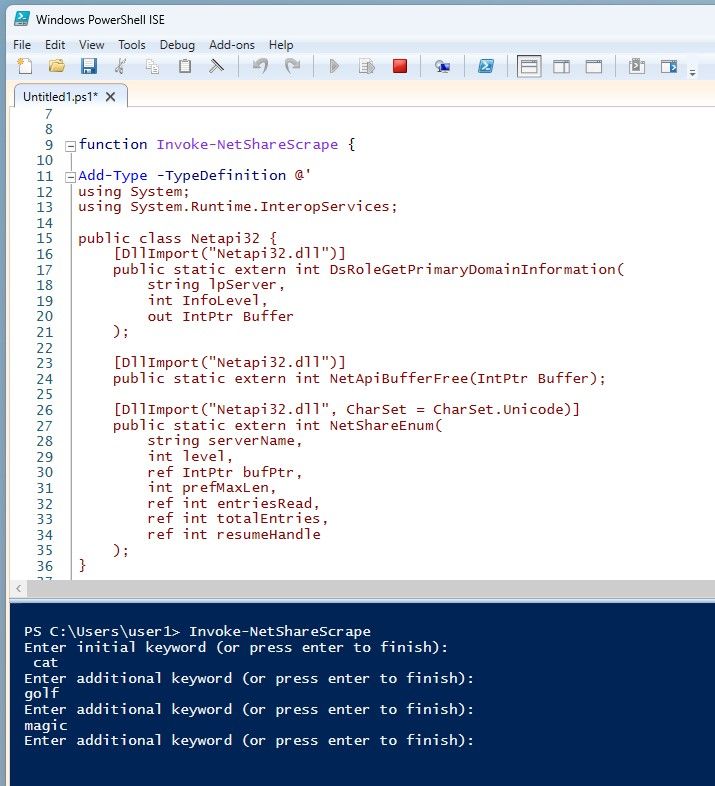
Invoke-NetShareScrape.ps1
This PowerShell script enables the search for specific keywords within network shares. It can be executed by a user who is only a member of the domain users group.
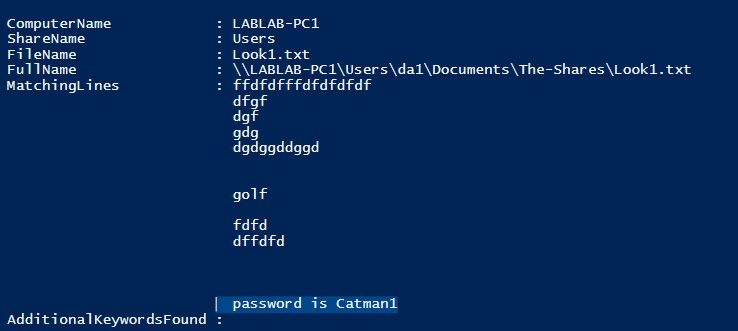
The script automatically retrieves a list of shares accessible to the user, and then proceeds to search for files that match the specified extensions. It reads the content of each file and utilizes regular expressions to identify lines that contain the specified keywords. For every matching file, it provides output including the computer name, share name, file name, file path, matching lines, and any additional keywords discovered.
Invoke-NetShareScrape Detailed Overview
NetShareScrape leverages .NET interop to access functions from the Netapi32.dll library, allowing the retrieval of network share details. Afterward, the user is prompted to enter search keywords using PromptForCustomKeywords. The script then iterates through each share and conducts a recursive search for specific file extensions (txt, ini, xml, bat, ps1, doc, docx, xlsx, xls), while excluding specific file names (GptTmpl.inf, GPT.INI, Registry.pol). Upon finding a matching file, it reads the file content and employs regular expressions (Select-String) to identify lines containing the specified keywords. When a match is detected, a custom PowerShell object is created, encompassing properties such as computer name, share name, file name, file path, matching lines, and additional found keywords.
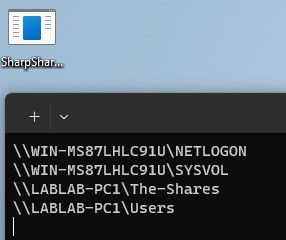
SharpShares
SharpShares utilizes LDAP to retrieve the computer names within a domain. It subsequently performs an enumeration of shared folders on each computer by invoking the NetShareEnum function from Netapi32.dll. The tool excludes administrative shares (ADMIN$, C$, IPC$) and provides a list of the remaining shared folder paths.
It enables automated enumeration of domain shares for which you have read access.
Invoke-Ghost.ps1
Invoke-Ghost is a tool designed to extract metadata from Microsoft Office documents. By utilizing the Shell.Application COM object, it retrieves valuable information such as the author, creation date, and last modified date of each file within a specified directory.
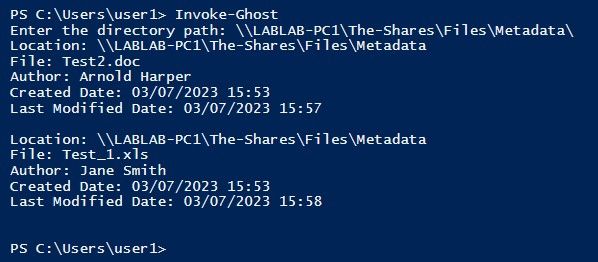
The 'author's name' parameter often contains the user's account name, making Invoke-Ghost a stealthy tool for harvesting potential usernames. Leveraging this feature, it provides an effective approach to extracting usernames from Microsoft Office documents.
Wrapping Up
We dedicated significant time and effort to developing and preparing these tools, but our commitment doesn't stop here. We have ambitious plans to continue expanding and enhancing our toolkit with even more powerful functionalities.
The Adversary Kit provides powerful tools for both pen testers and defenders to navigate the intricate landscape of active directory domains.



