I Know What Your Password Was Last Summer...
We have spent the last six months researching on the previous two years of prior cracked passwords and built some tools to understand password creation strategies better. Here are the results.

As security professionals, we often run into the age-old issue of passwords across multiple environments, systems, implementations, and other chaos. An interesting aspect we regularly encounter when compromising organisations is the psychology behind how people choose their passwords. This insight reveals patterns and tendencies in password creation within windows environments, shedding light on common vulnerabilities and the human factors influencing password security.
Understanding these psychological elements is crucial for developing more effective security strategies and educating users about safer password practices. It is equally important when building cracking methodologies to effectively assess an organisation's security posture and crack the keys to the kingdom.
This post delves into the trends identified over the past two years, offering insightful comparisons between strong and weak password policies. It also explores the user behaviors that develop due to these policies.
We use hashcat as a strategic and systematic approach to advancing our engagements over time, particularly in the realm of cracking password hashes. This method has proven effective in obtaining the cleartext values for various interesting passwords, providing valuable insights into organisations' trends and practices in establishing their password policies.
Additionally, this approach informs our strategies for password guessing and spraying attacks against endpoints, enhancing our understanding of the thought processes prevalent in specific industries and how certain security controls can be bypassed.
The Core Data
All of the analysis in this post is from an amalgamation of cracking windows NTLM passwords over two years; the total amount of hashes was 186149, unique hashes were 99918, and 31200 were cracked, resulting in many repeat passwords across users and industries.
The findings from this extensive data set offer valuable insights:
- Password Reuse: The large number of repeat passwords suggests a widespread issue of password reuse across different users and industries, a practice that significantly compromises security.
- Common Weak Passwords: The success in cracking a substantial portion of the hashes indicates that many users continue to rely on weak passwords, which are vulnerable to cracking tools and techniques.
- Industry Patterns: The data potentially reveals patterns in password creation and policy enforcement across various industries, providing an understanding of industry-specific security postures.
Our Hashcat Rules and Setups
Depending on the hash type will depend on how we approach cracking it on our rig; typically, quicker to crack hashes such as NTLM, we will approach with a wordlist for a quick flyover followed by rules, followed by specifics around the company name, and other relevant wording or phrases.
Our collective NTLM cracking rate is ~600GH/s, comprised of several RTX 4090s, 3090s, and other cards.
We use a collection of custom and standard wordlists when targeting organisations. The standard public lists we try with various rules are shown:
- HaveIBeenPwned password list from PwnedPasswords (https://github.com/HaveIBeenPwned/PwnedPasswordsDownloader)
- Common Corp Passwords (https://github.com/danielmiessler/SecLists/blob/master/Passwords/common_corporate_passwords.lst)
- English Dictionary (https://github.com/dwyl/english-words/blob/master/words.txt)
- Crackstation (https://crackstation.net/crackstation-wordlist-password-cracking-dictionary.htm)
- Antipublic (https://bigpasswordlist.com/DAAP.html)
- Weakpass_3a (https://weakpass.com/wordlist/1948)
As for rulesets, we use public and private ones again, but here are the public ones we use:
- OneRuleToRuleThemAll (https://github.com/NotSoSecure/password_cracking_rules)
- OneRuleToRuleThemStill (https://github.com/stealthsploit/OneRuleToRuleThemStill)
- Pantagrule (https://github.com/rarecoil/pantagrule/tree/master/rules/private.hashorg.royce)
Finally, on top of wordlists and rules, there are some custom masks we frequently use when targeting specific organisations, but there is a core list of masks and hashcat commands:
CompanyName?a?a?a?a?a?a
Colour?a?a?a?a?a?a
A prevalent trend observed in various environments is the use of situational or time-structured passwords. Users often create passwords incorporating elements such as the current season, month, day, company, or department name, typically followed by a date. This predictable pattern makes it easier to crack these passwords using hashcat rules and masks, allowing for efficient and swift password reversal.
Andy Gill, one of our consultants, wrote a toolkit for parsing pot files that we've leveraged to build master wordlists and standard rules:
The crack flow process typically follows targeting the company with a select wordlist and rulesets, brute-forcing up to the nine-character keyspace with optimized keyspace, parsing the profile, and running the cracked list against a ruleset again to fish out patterns.
What was your password last summer?
As companies mature, so do their password policies; gone are the days when many of our clients were simplySummer2024! , and you're in the front door. We still see SeasonYYYY or variations of it in less mature environments now and again. Here are some of the examples we've seen of seasons and mentions of them:
We wrote an in-house tool to do password analysis. When given an input of cracked hashes, it would analyze common words, phrases, and other attributes. The results from said tool are shown in the following screencaps detailing common passwords, top passwords, days of the week, months of the year, seasons, and colours.
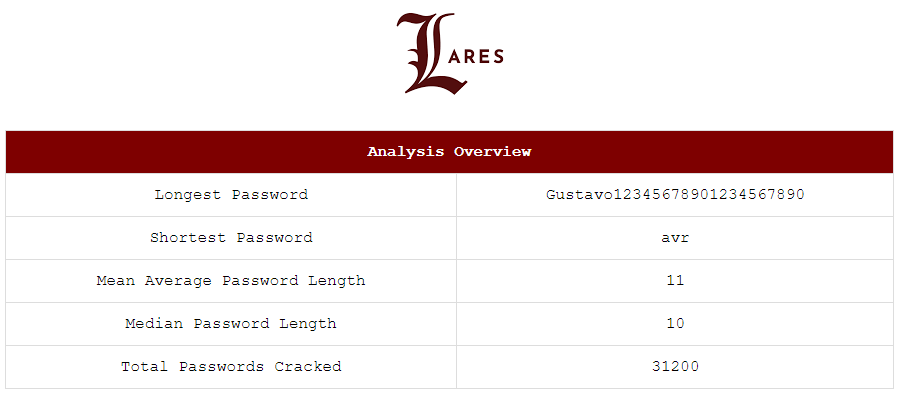
The average length of 11 characters shows a good improvement year on year and more mature password policies being applied across organisations. While there are still outliers, the general coverage of estates looks to be on an upward trajectory for improvement.
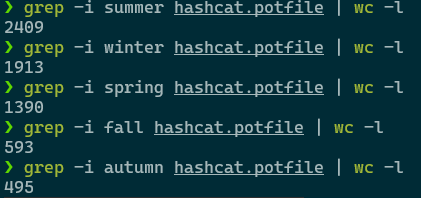
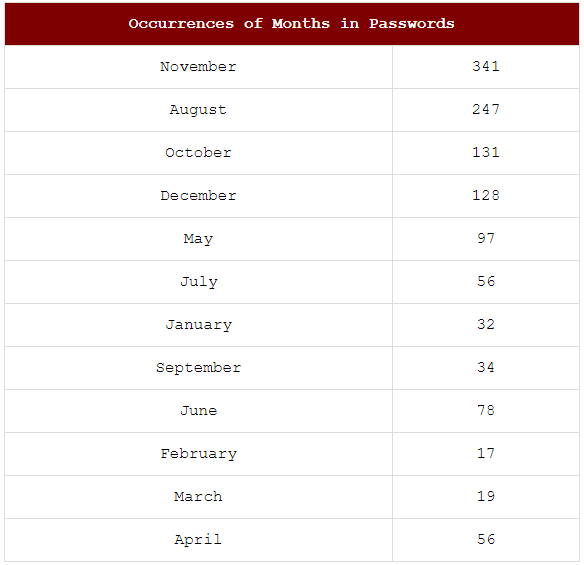
Despite people being big fans of summer, it would appear the winter months are more prevalent in passwords.
The title of this post gives it away, but people are big fans of summer, and it's apparent in their password creations, too.

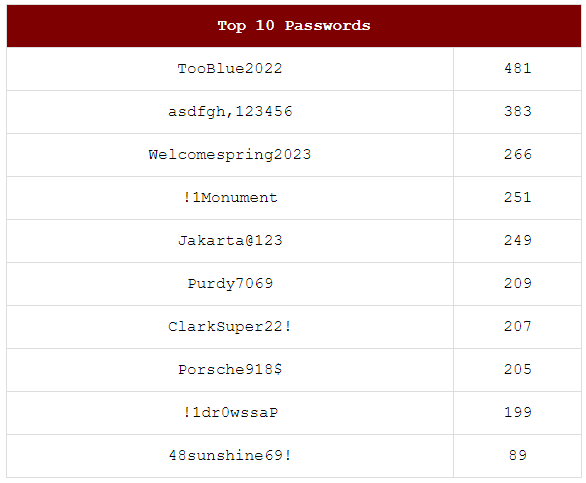
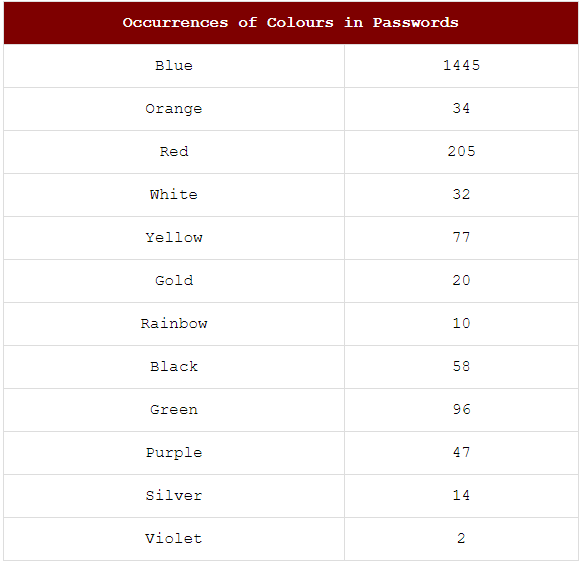
Many folks have a favourite colour of blue, with red and green following closely behind.
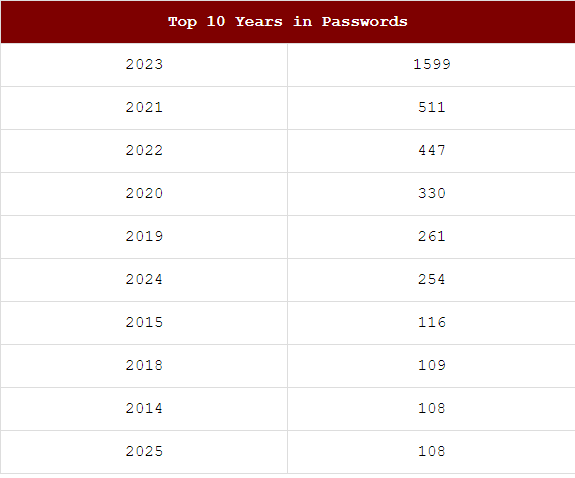
Of the top years in passwords, 108 were forward thinkers, getting that 2025 several years ahead; attackers will never think of that!
Interesting Passwords
We come across many interesting passwords; here are some of our favourites we've seen in the last couple of years, both secure and funny.
<Passw0rd1><Passw0rd2>
#1PeppermintPatty
Grits&Gravy4u
HelloSummertime2023!
Security4You
Sec9re_NobodyWillGuessMe
Gustavo12345678901234567890
Green eggs and ham!
Why $o Serious?
These passwords were cracked using a combination of mask attacks, wordlist and rule-based attacks. In addition, baseline password lists were used iteratively to crack and inform cracking other passwords. Remember that complexity and length can make cracking time-consuming and resource-intensive, especially with high-entropy passwords.
Further Analysis on Duplicates
Our analysis revealed significant findings regarding duplicates and unique users with shared passwords. A recurring pattern was observed where accounts set up by an organisation for specific purposes shared identical passwords, often resulting from mass-reset procedures.
Additionally, instances were noted where users with multiple accounts, especially those with privileged access, reused passwords across different organisations. The research also sheds light on cases where users, upon changing organisations, continued to employ poor password practices, carrying the same weak passwords to their new workplaces.
- Total Hashes: 186149
- Total Duplicate Hashes: 56648
- Total Users with Duplicate Passwords: 11359
The successfully cracked passwords were analyzed on publicly available lists from SecLists(https://github.com/danielmiessler/SecLists/tree/master/Passwords/) to uncover interesting matches in public wordlists.
2020-200_most_used_passwords.txt: 19 matches
2023-200_most_used_passwords.txt: 20 matches
500-worst-passwords.txt: 39 matches
bt4-password.txt: 212 matches
cirt-default-passwords.txt: 7 matches
clarkson-university-82.txt: 7 matches
common_corporate_passwords.lst: 118 matches
darkc0de.txt: 135 matches
darkweb2017-top10.txt: 5 matches
darkweb2017-top100.txt: 9 matches
darkweb2017-top1000.txt: 54 matches
darkweb2017-top10000.txt: 161 matches
days.txt: 17 matches
dutch_common_wordlist.txt: 105 matches
dutch_passwordlist.txt: 724 matches
months.txt: 48 matches
Most-Popular-Letter-Passes.txt: 94 matches
mssql-passwords-nansh0u-guardicore.txt: 118 matches
openwall.net-all.txt: 143 matches
probable-v2-top12000.txt: 148 matches
probable-v2-top1575.txt: 65 matches
probable-v2-top207.txt: 26 matches
richelieu-french-top20000.txt: 104 matches
richelieu-french-top5000.txt: 67 matches
scraped-JWT-secrets.txt: 8 matches
seasons.txt: 40 matches
twitter-banned.txt: 34 matches
unkown-azul.txt: 9 matches
UserPassCombo-Jay.txt: 23 matches
xato-net-10-million-passwords-10.txt: 4 matches
xato-net-10-million-passwords-100.txt: 16 matches
xato-net-10-million-passwords-1000.txt: 53 matches
xato-net-10-million-passwords-10000.txt: 121 matches
xato-net-10-million-passwords-100000.txt: 284 matches
xato-net-10-million-passwords-1000000.txt: 525 matches
xato-net-10-million-passwords-dup.txt: 523 matches
xato-net-10-million-passwords.txt: 755 matches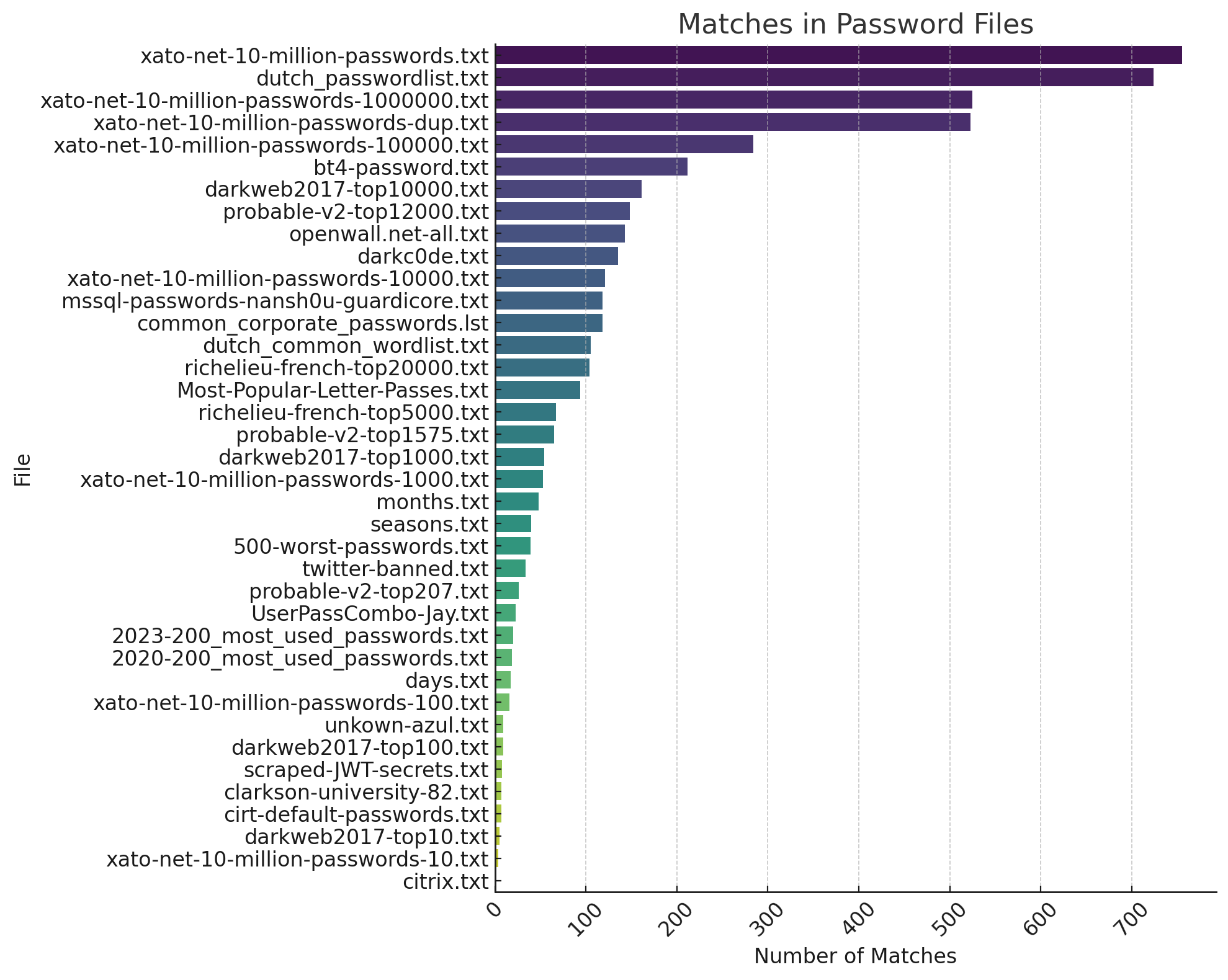
The results indicate that all the passwords identified are already known and included in standard wordlists. This suggests a greater likelihood of successful compromise by attackers.
Advice For Password Creation
When selecting a password, conventional advice has long recommended using a mix of special characters, numbers, and upper and lower case letters, with a minimum length of 8 characters. However, this advice evolves. Observations from our more mature clients indicate that prioritizing password length over complexity and less frequent changes encourages the adoption of passphrases. These are easier to remember yet remain challenging to crack, offering a balance of security and user-friendliness.
Both the UK and US government security arms have great advice around password creation; therefore, here is a combination of their advice to help you create strong passwords:
- Length is significant; aim for a minimum of 16 characters when creating an active directory policy.
To help users with creating long passwords, try suggesting using four random words and connecting them with a special character like a - or $, doing so increases the complexity and at the same time the length. An example of this may be:
Sunset$Guitar$Puzzle$JourneyorCloudy-Envelope-Rainbow-Dinosaur(Don't use these two examples as they're also on our wordlist ;) )
Both of these would fall within a decent length as the phrase "Cloudy-Envelope-Rainbow-Dinosaur" consists of 32 characters, including the hyphens, and "Sunset$Guitar$Puzzle$Journey" consists of 28 characters, including the dollar signs.
2. When setting up default or initial passwords for the organisation, it is advisable to use an algorithm for generating unique user passwords, rather than relying on a static value. If implementing such an algorithm is not feasible, an alternative approach is to require users to change their password upon their first login. This practice helps in minimizing security risks.
3. To ensure that users maintain unique passwords, it is beneficial to encourage and enforce the use of password managers. These tools assist not only in generating solid passwords but also in creating distinct and unique passwords for different accounts. This approach steers users away from easily crackable passwords, such as basic phrases, common words (like 'welcome' or 'password'), seasons, months, years, and places. Instead, users can opt for the recommended method of combining four random words, which can then be securely stored in a password manager. This strategy enhances overall password security and management.
Conclusion
This post has primarily focused on the security of passwords within Windows environments, particularly from an internal standpoint using data collected across many datasets. However, it is vital to stress that a robust password policy should not be an organisation's sole line of defence. In addition to strong passwords, it is imperative to implement further protective measures.
Key among these is the adoption of multi-factor authentication (MFA), which adds a layer of security beyond just the password. MFA requires users to provide two or more verification factors to access a resource such as an application, online account, or a VPN. This significantly reduces the risk of unauthorised access. Where possible, we have seen some clients implement MFA for access to internal resources, utilising existing single sign-on providers and similar identity and access management technology to restrict lateral movement opportunities.
Moreover, organisations should embrace the principle of 'defence in depth'. This is a comprehensive approach to cybersecurity that layers multiple defensive mechanisms. If one mechanism fails, another steps in immediately to thwart an attack. This approach involves technological solutions and encompasses policies, procedures, and awareness training to ensure that all possible security gaps are covered.
Incorporating these practices alongside a robust password policy creates a more resilient and secure environment, reducing the likelihood of successful cyberattacks and enhancing overall organisational security.


