Social Profiling – OSINT for Red/Blue
One of the areas that I love when it comes to red/purple engagements is profiling organizations on LinkedIn and GitHub, looking for crucial information that can lead to more juicy enumeration.
This post will give you an overview of key things to look for from an offensive and defensive perspective to look out for employees, interns, and contractors over sharing information on projects and technologies.
For all the examples, either Lares or an example organization has been used. The two main techniques below are active and passive open-source intelligence gathering (OSINT). Also, as an attacker on the internet, I can be whoever I want to be at any point. One day I may be a recruiter, but the next, I may be an HR professional who worked for your organization for many years to build user trust.
There are a few key areas when it comes to open OSINT where LinkedIn is helpful; the first fall under active OSINT, whereby an attacker will connect to the HR department at a target organization with the primary focus on gaining other connections within said company. The logic is that the more links a user has within a company, they can further their trust within the target. When sending a connection request to a user on LinkedIn, if the recipient sees the sender has multiple mutual connections, they are more likely to trust them.
LinkedIn, on its own, is a goldmine of information ranging from information about the target company, such as headquarters which in turn allows an attacker to work out the time zone of targets. It also shows a rough estimate of the number of employees working for the company and often the company website. Below is an example of Lares’ profile on LinkedIn.
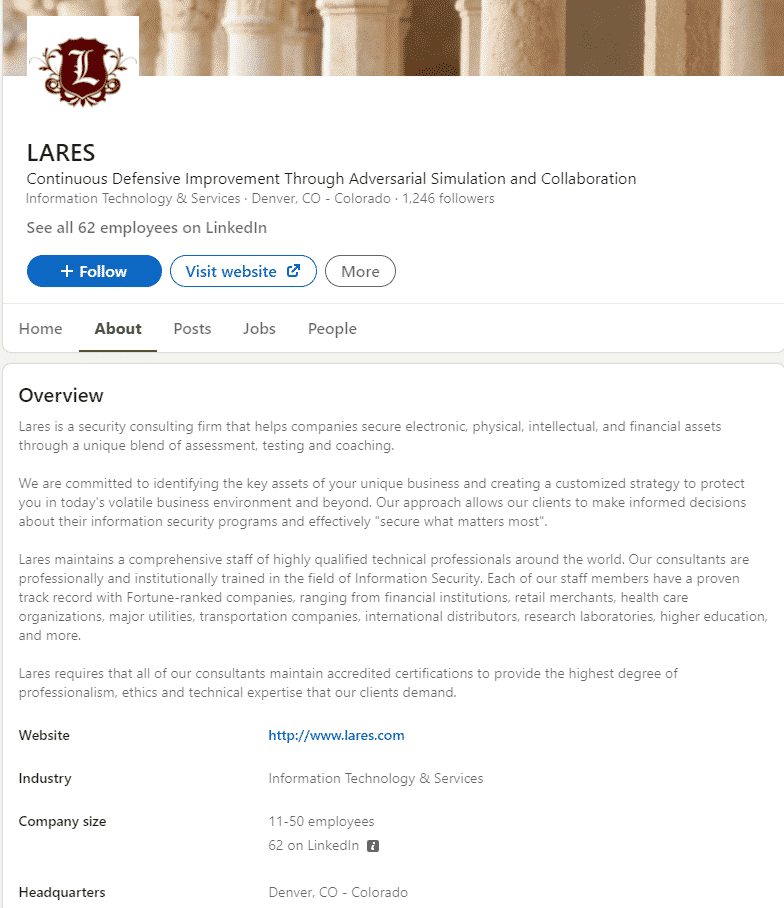
From Lares’ profile as an attacker, I can work out that the head office operates in Denver, CO, USA (GMT-6), which is essential if I want to phish or target specific users at the correct time of day. We can also see that the organization is relatively small, altering the type of phishing campaign or social engineering carried out. Scrolling down the page further will sometimes show more locations on a world map which is invaluable to an attacker.
Building Rapport
Upon connecting with users in a target organization, a second technique often used in social engineering is building rapport with a target. This may be via connecting with specific users to find more on their profile about the company or expand the mutual connections to uncover information about a company or the technologies in use.
Typically on an initial look at a company, depending on the size, there will be minimal mutual connections, and the key staff in IT/Dev will usually have their privacy settings turned up to full, so they show as ‘LinkedIn Member’ like below for LARES employees:

However, once connections are made within the company, they will show up as 2nd or 3rd connections with ‘shared connections', in the example below, Chris’ profile shows as a second connection with 68 shared connections:
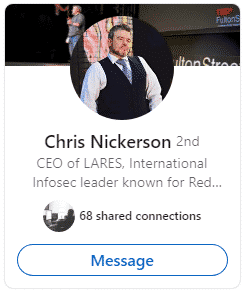
We can use mutual connections as leverage to identify more about a company. Once the connections are made, we can start to look into how much users are disclosing on their profiles; a common point to look at is job adverts and previous job experience. Simply searching for summer intern "company name" will return much information. As shown below, we have an example user disclosing quite a lot of info about their IT internship at ACME Corp:
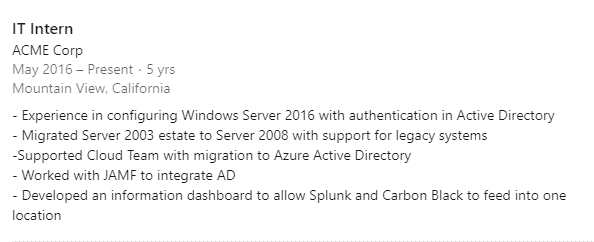
As an attacker, this kind of information is a goldmine; it tells us straight away that the company is likely using a Windows estate with some MacOS in use (due to the mention of JAMF); it also discloses information about Azure being used and security products. Nobody wants to blame the intern as we saw with SolarWinds; however they do like telling the world what they have achieved.
There are many other ways LinkedIn can be used for OSINT, like finding past employees and looking to assume the persona of specific people in departments; however this post won’t dive into that.
Threat Actors Using in Wild
Another reason for both red and blue teams to learn these techniques is that threat actors use the same methods in the wild. The link below details insight into the UK-based Centre for the Protection of National Infrastructure (CPNI) discovery of foreign threat actors using LinkedIn to target MI5 agents.
GitHub
The second site and technique that lands us a lot of success is searching GitHub for a multitude of information. There are automated tools out there to search through specific repositories and many Twitter accounts and services for hunting for open repositories and keys that are disclosed; two examples are:
Both will let you view potential leaks in generic repositories and look for high-entropy strings. Other tools, such as TruffleHog will allow you to clone specific repositories and search for keys and passwords; however, automating the solution can be helpful for quick wins. One of the interesting points worth noting is Leak Scavenger will call out leaks in other services that aren’t just git however, it will alert to high entropy strings that could be of use from a red team perspective.
Search Terms
Regarding attacking companies and building up recon from a passive perspective, we have a lot of success via manually crafted searching and specific search operators similar to Google Dorking. Usually, initially searching for the company domain on Git will yield a lot of results; see the below for lares.com:
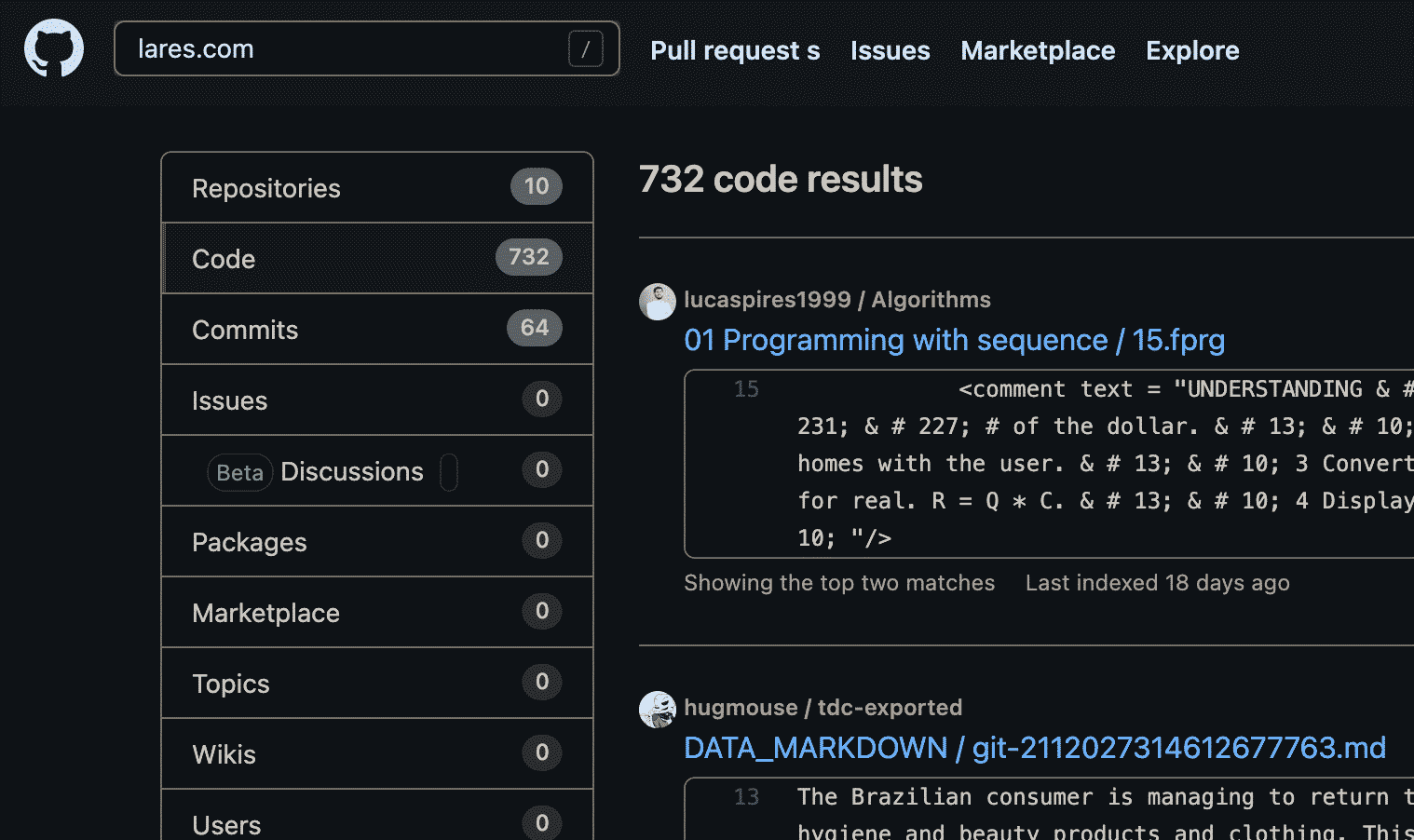
There are a few results; however, if we want to hone in on specifics about the domain, we might combine it with other words and operators such as "lares.com" "password", which in this example returns a repo with some juicy looking data:
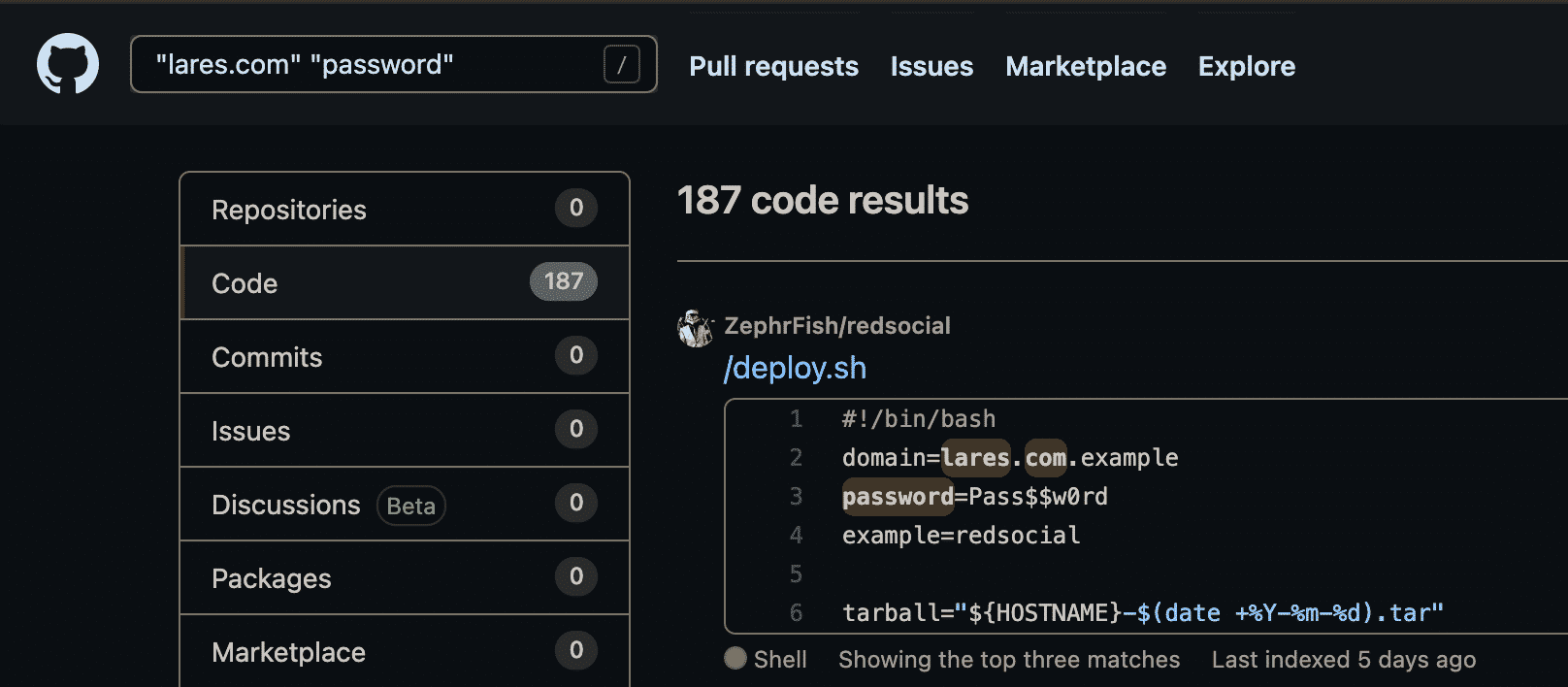
As can be seen in the example above, deploy.sh discloses a few key interesting pieces of information. If we wanted to dive a little deeper into this particular user and see other repos that they had published, mentioning the target domain, a search like user:zephrfish "lares"would match all instances of lares within the user’s repositories:
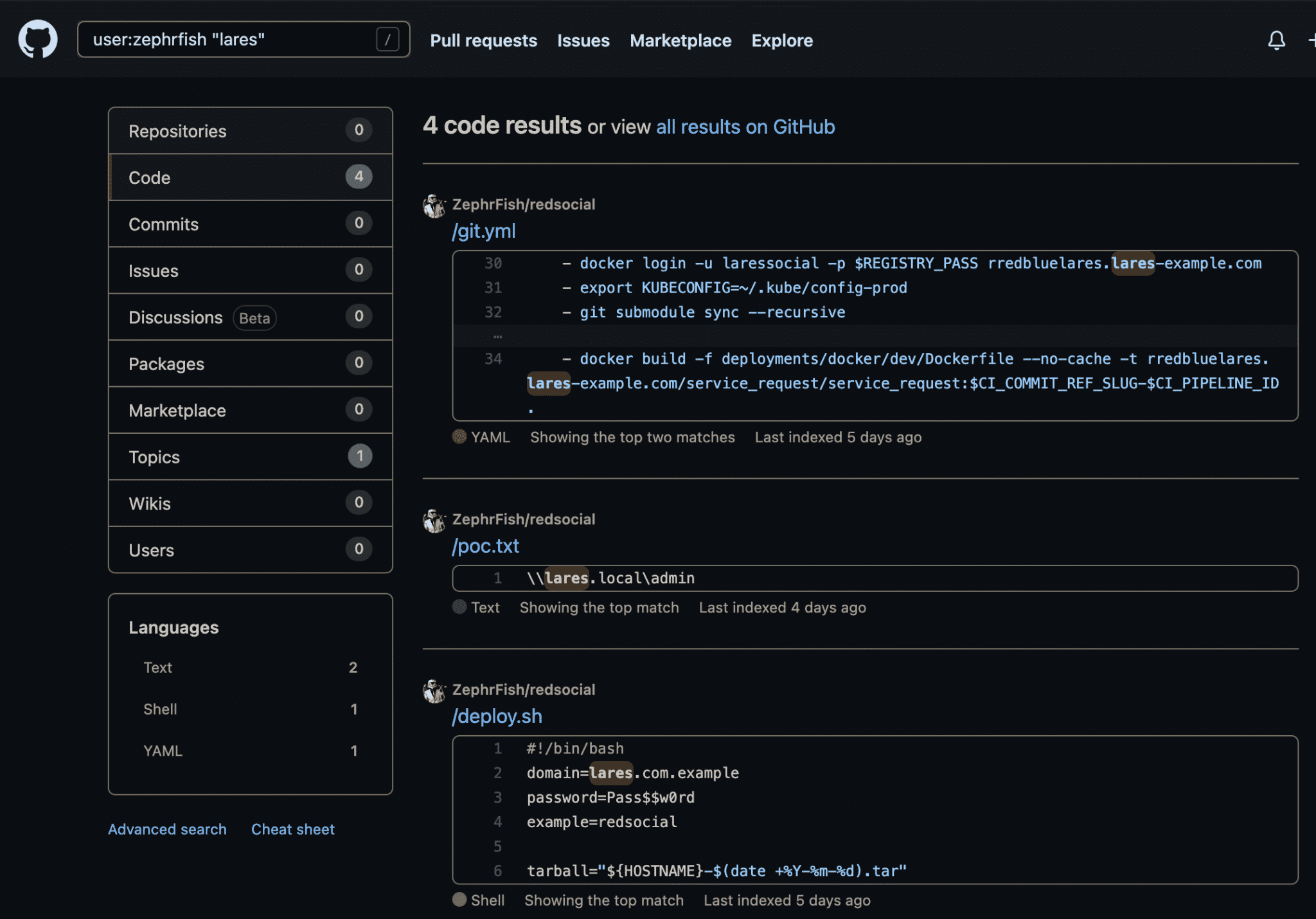
If we look at the second repo in the image above, there is code for poc.txt which discloses lares.local and this can be combined with other operators to search for more in depth information such as + or additional terms in double quotes.
Finding users that work for an organization can sometimes be difficult. However, combining information from LinkedIn, Twitter and other platforms, we can sometimes work out a user’s profile on multiple platforms and search their code repos for specifics that may lead to information about internal systems, coding practices, technologies, and in some cases, credentials.
Active Defense
While searching for this information is incredibly useful from an attacker's perspective, it can also be useful for defenders to carry out from time to time to analyze an organization’s threat profile.
In addition to profiling an org, additional active defense measures can help alert when profiling occurs. This can be done by leveraging canary tokens in the form of fake keys or credentials that, when used, trigger alerts on your SIEM. Thinkst Canary offers a free service to generate tokens that can be placed anywhere and alerted upon when used.
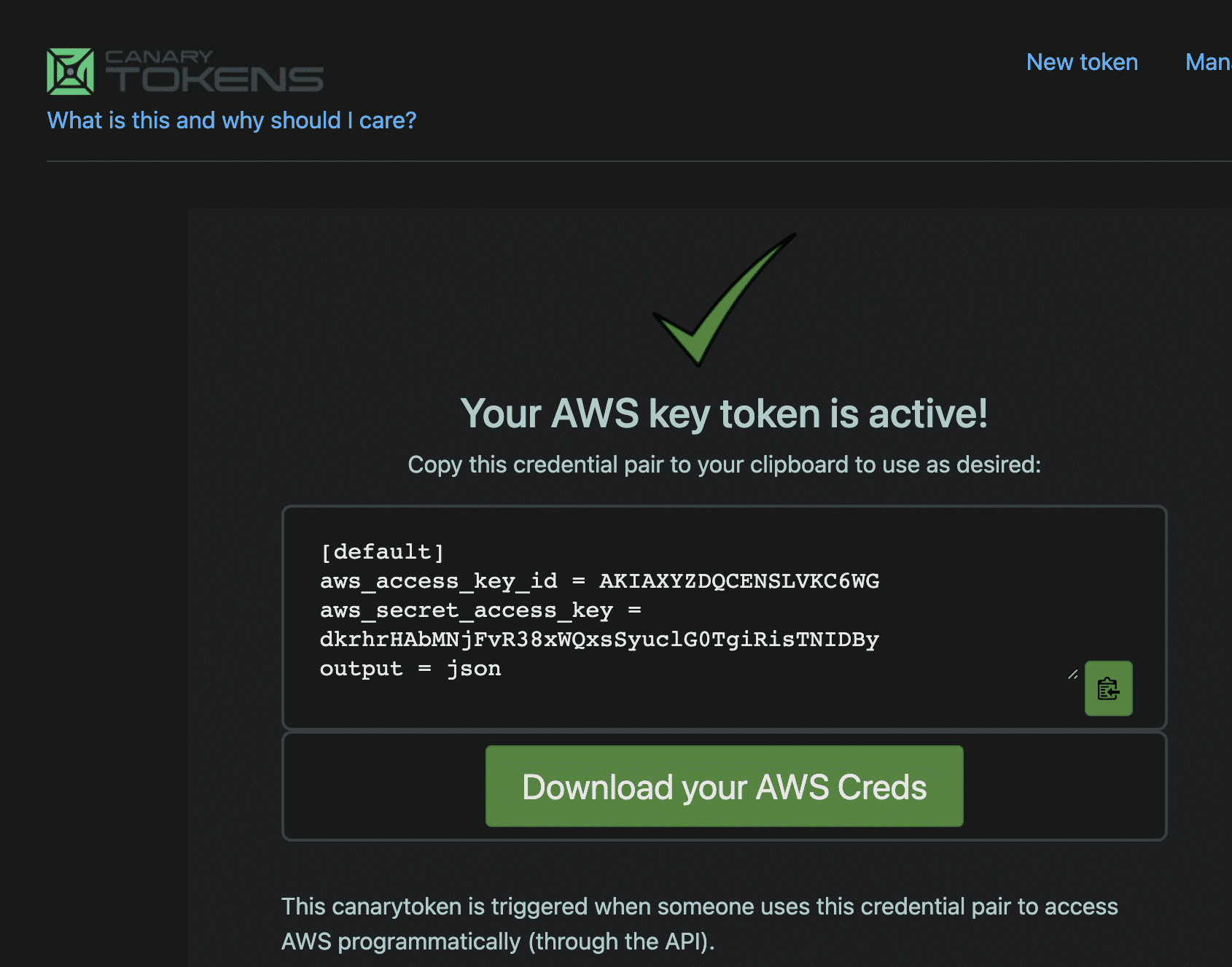
As seen above, we can generate canary tokens for AWS keys and place these within a repo so that an alert is triggered when the key is used, thus achieving active defensive techniques.
Conclusion
Whether you are operating from an offensive or defensive perspective, understanding an organization and the personnel working for that organization is incredibly important for carrying out recon. Both GitHub and LinkedIn are invaluable resources for this very purpose, but they are not the only options; we use many other tools at Lares for passive and active reconnaissance.
Specifically, when looking at followers or connection requests on LinkedIn/GitHub from a corporate perspective, always be alert for potential threats and risks of connecting to folks you do not know, as they may not be who they say they are…

