Introducing Super Sharp Shares
SuperSharpShares is a tool designed to automate enumerating domain shares, allowing for quick verification of accessible shares by your associated domain account.

Back Story
SuperSharpShares came about somewhat unexpectedly - it was never intended for release and wasn't initially developed with that goal in mind. Originally, it served as a solution within a more intricate tool we created that remains unreleased (for now, never say never). However, during a challenging assessment due to the scale of the environment, the automated share enumeration functionality was attractive as something to run quicker than other tools. As such, we copied that functionality and then used it to create this standalone program.
While numerous tools offer similar functionalities, our preference, where possible, is to develop our tooling in-house. This kind of hands-on approach gives us a better understanding of how something works and enables the opportunity to change or tweak it as required. Releasing the tool allows others to ignore, tweak, or improve as they feel fit.
If we had to sum up the advantages of SuperSharpShares. They are as follows:
- easy to use,
- quick, even within large environments,
- suitable for auditing,
- A small data footprint with minimal lines of code makes it easier to understand how it works and use it in other projects.
Again, numerous tools offer similar functionalities, but they are often bundled within a more extensive tool offering; it is nice to have a single function within a tool to help keep it simple.
As the saying goes, “A picture is worth a thousand words,” with that, it's best we just show you SuperSharpShares after execution.
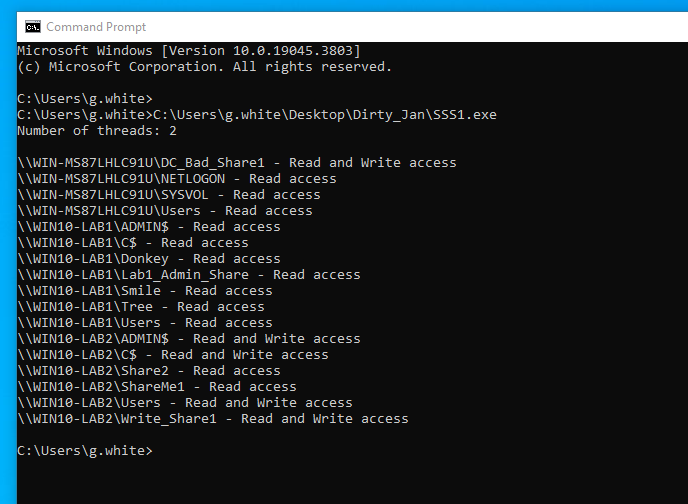
Execute SuperSharpShares from a domain-joined host or a runas window, both with no command options required. The program automates the entire process for you: the domain look-up, host machines, accessible shares, and finally, each available share or write access status. We have used SuperSharpShares across multiple domains, and even in large environments, we've observed that it swiftly enumerates accessible shares quicker than many other tools.
Read and Write Access
Domain shares are filled with gold; in almost every environment, examples of sensitive data are being overly shared. Armed with a typical user's domain account, adversaries can often access enough internal data to tarnish the business name, manipulate a business's share price, encrypt data for a ransom, or snoop.
During an assessment, it's common to uncover read access to shares that were either unknown or intended to be accessible only by a specific group of individuals.
Having write access to a share implies the ability to make unauthorized changes to files or folders, allowing manipulation or injection of malicious content. Notably, write access to an ADMIN$ or C$ share often signifies that the executing account potentially possesses administrative privileges over the identified host.
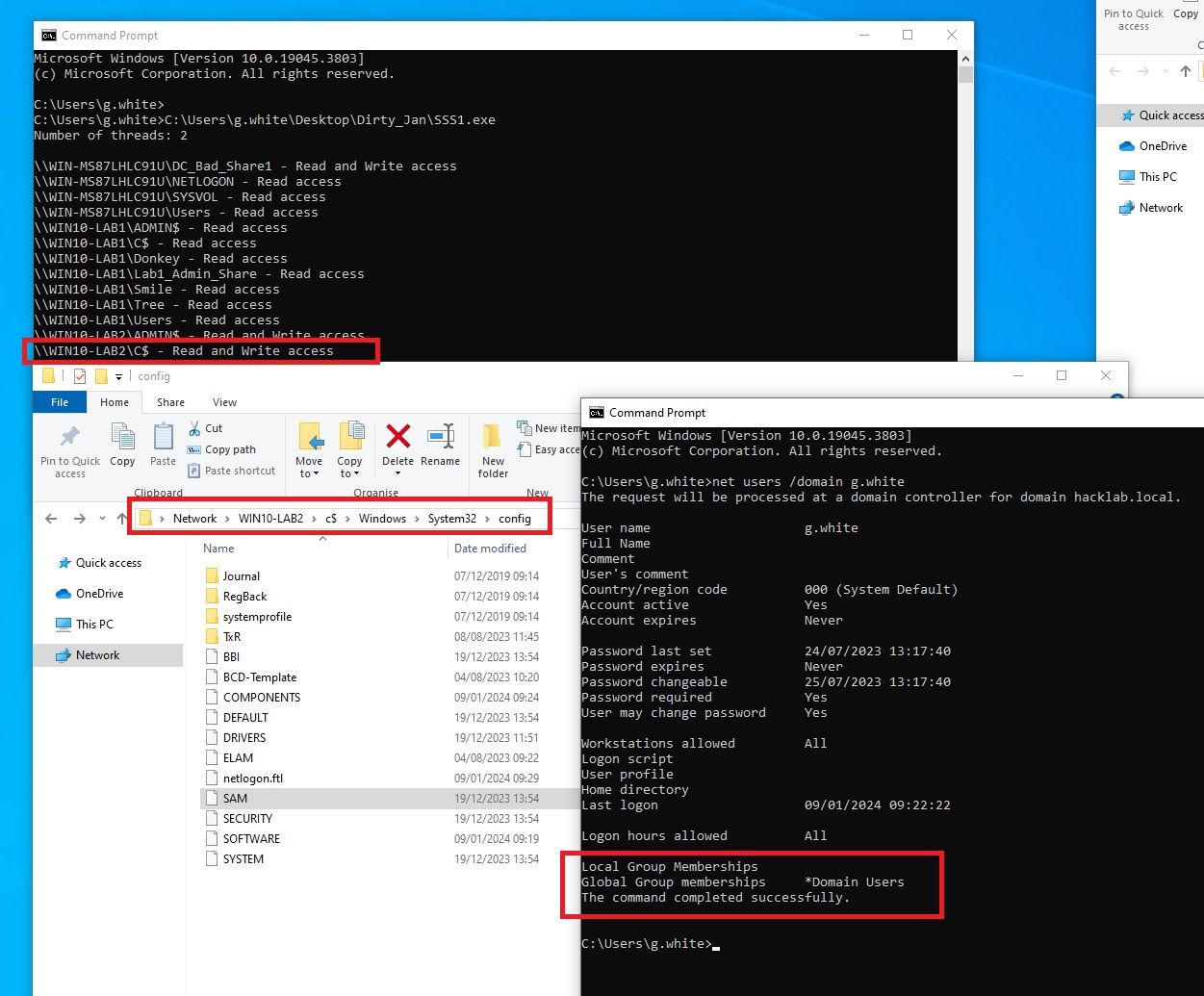
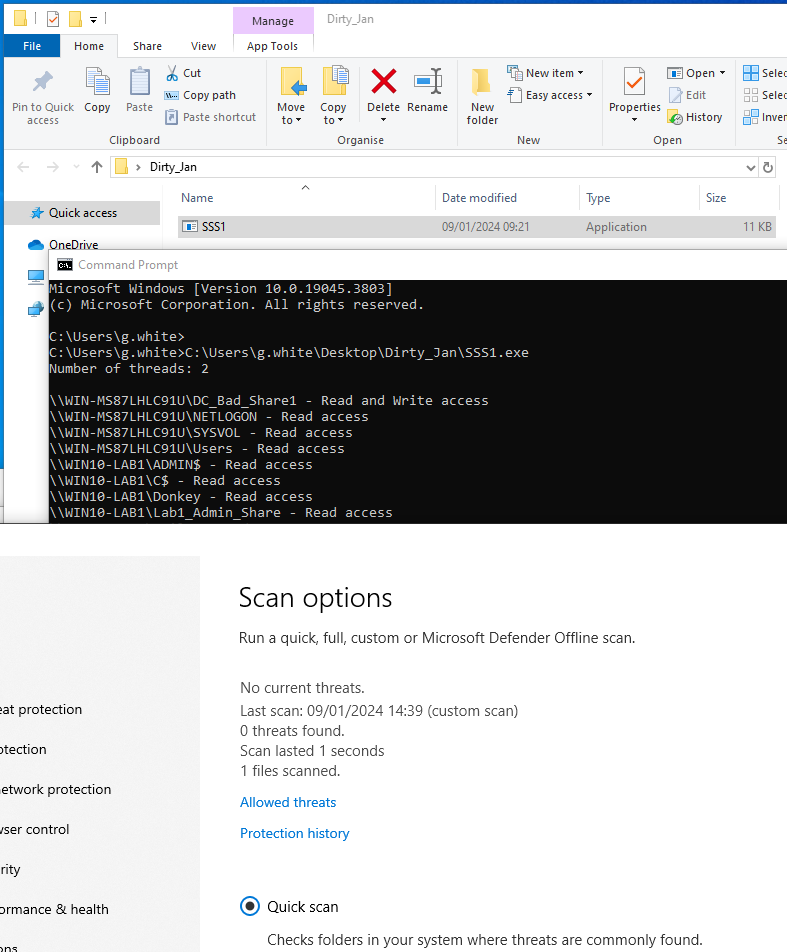
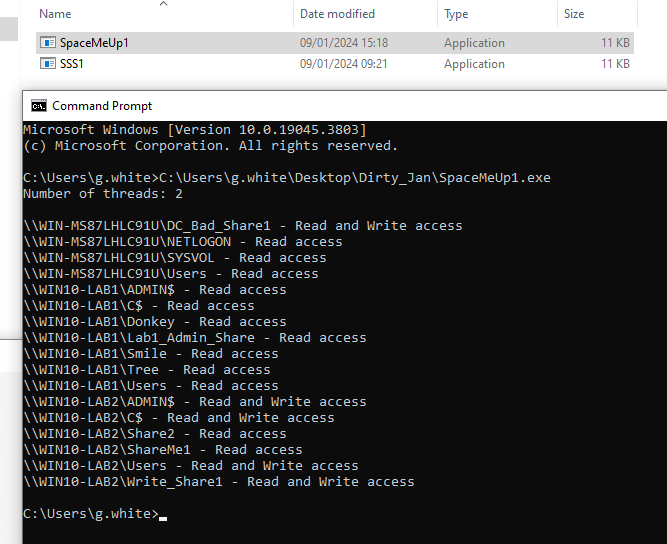
The picture below details the following:
- The execution of SuperSharpShares has revealed Write access to the
C$share on hostWIN10-LAB2. - Windows File Explorer is used to manually access the share, verifying the administrative access to the host.
- The final CMD prompt confirms that the executing account is only a member of
Domain Usersgroup.
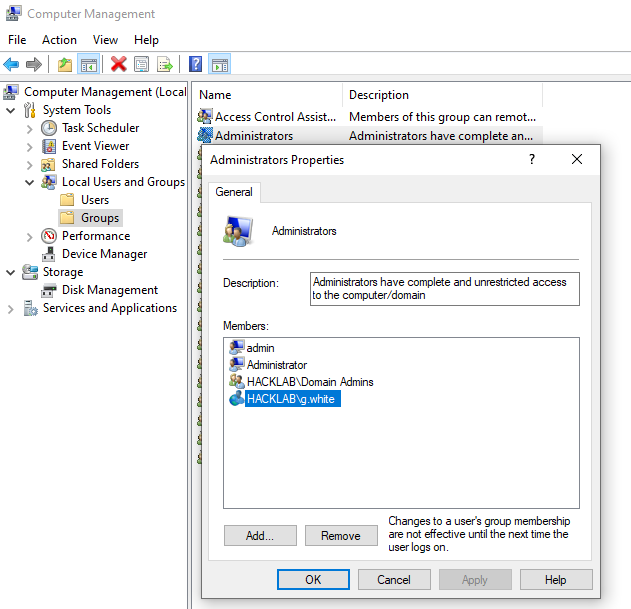
In large environments, it's common to discover an individual domain user account or the whole group has been added to a machine's local administrative security group.
SuperSharpShares Under The Hood
The program starts by retrieving the domain name associated with the currently logged-in user.
After obtaining the domain name, the program calls the GetComputerNames method, which is part of the EnumerateDomainShares class. This method queries Active Directory for computer objects within the specified domain and retrieves a list of their host names.
The GetComputerNames method uses an LDAP path and Active Directory queries to fetch the list of computer names within the enumerated domain.
The NetShareEnum function from the Netapi32.dll library is then used to enumerate and retrieve information about the accessible shared resources (shares) on each enumerated computer within the domain.
The script utilizes the Parallel.For construct, a mechanism provided by the Task Parallel Library (TPL) in C# to help perform parallel processing.
The TPL automatically manages the allocation of threads based on the available CPU cores. The idea is to divide the workload (iterations of the loop) among multiple threads, allowing concurrent execution to speed up the overall process; it works!
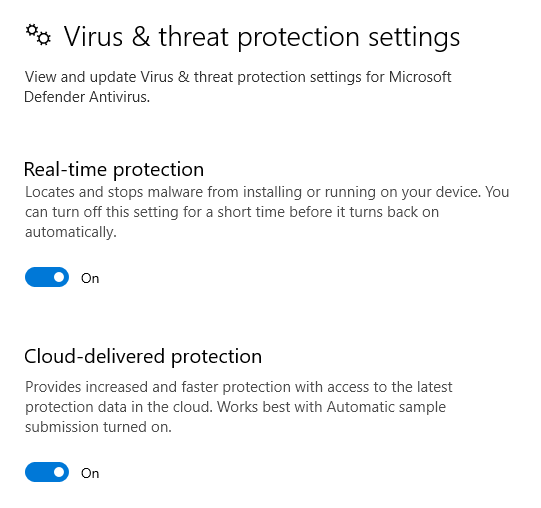
Endpoint Detection and Response
The program would be a valuable addition for any internal IT team to help them audit which shares are accessible by domain members.
While all included functionality is strictly legitimate, there is still a chance that the program could eventually be categorized as malicious by EDR solutions. At the time of release, there was no categorization by Windows Defender.
During a recent assessment of a very mature environment, we noted that SuperSharpShares was not blocked from execution but did raise a medium alert for potentially suspicious behavior due to the large amount of internal SMB connections to each host machine during the share enumeration phase.
This released version is intended for legitimate auditing purposes only and not super stealthy, sneaky red teaming assessments. This aside, we have verified in our lab that changing the method of execution from parallel to sequential means it does not perform multiple SMB requests at once, and then, in addition, adding a delay option would make the tool undetected. We have not added these options in the public release because it dramatically reduces execution speed.
Building
Double-clicking the SuperSharpShares.sln file should load all required to build the program.
Verify that the release has been selected on the top toolbar.
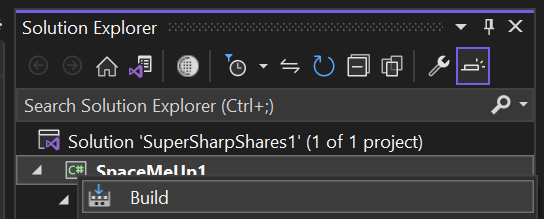
Under Solutions Explorer, right-click on the program and select Build.
Under the Output bar, you should see the build location.
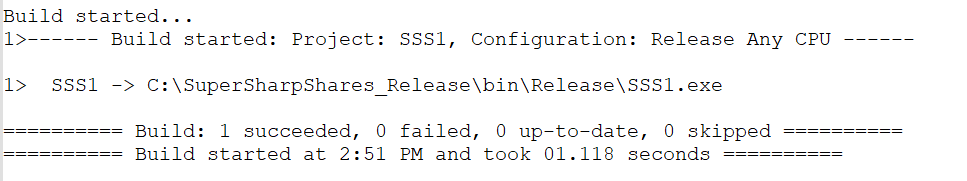
Good Practice
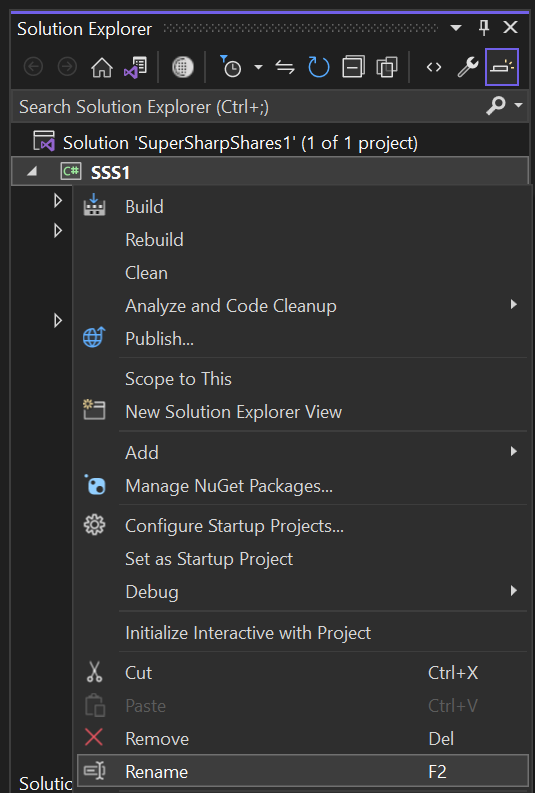
Following verification that the initial build was successful, you may wish to rename the program as such.
- Right-click on the program name under Solutions Explorer and select Rename.
2. Right-click on the renamed program under Solutions Explorer right-click and select Properties.
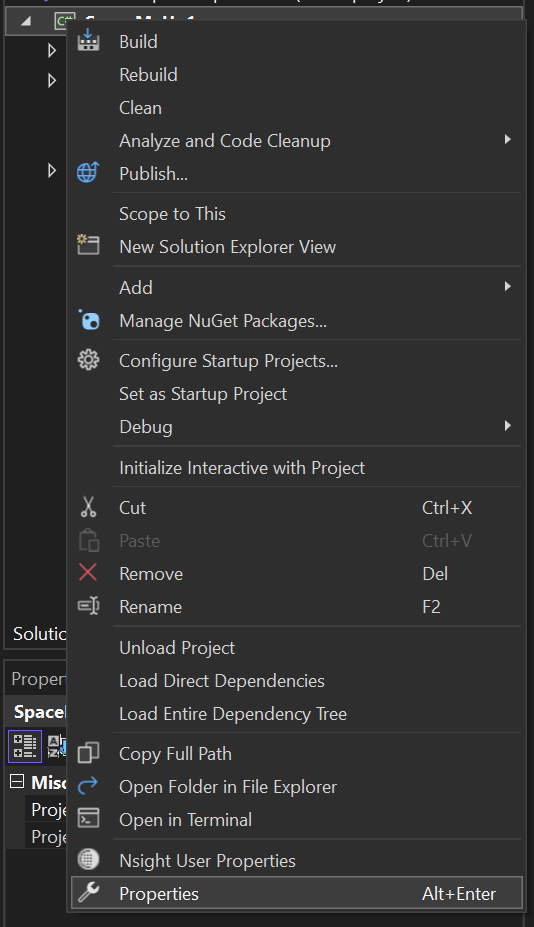
3. Change the Assembly name and Default namespace in the Application tab.
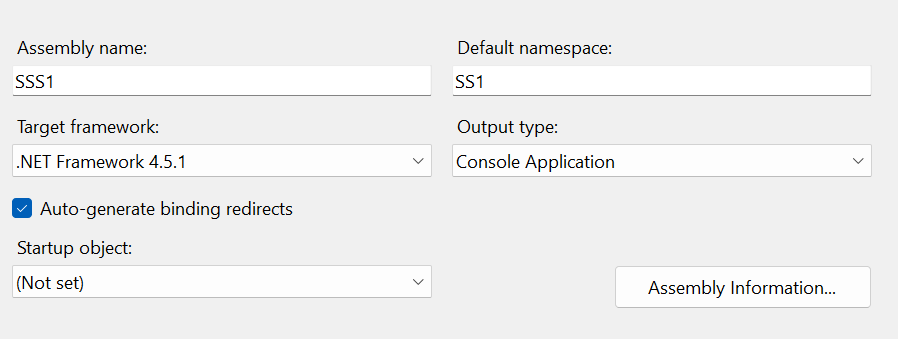
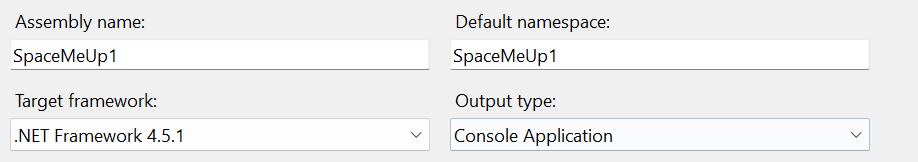
4. Back under Solutions Explorer, maximize Properties, and select AssemblyInfo.cs.
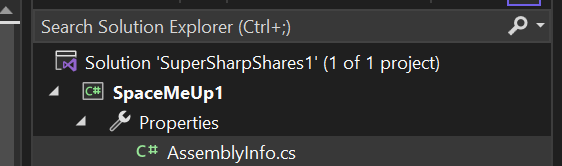
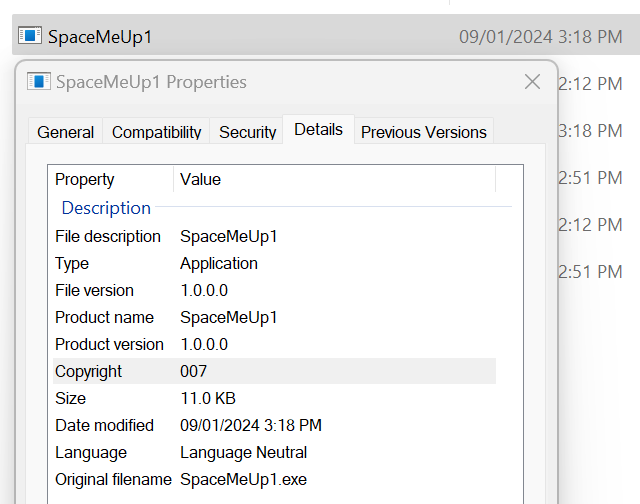
This should load the AssemblyInfo.cs parameters of which you may wish to edit the AssemblyTitle, AssemblyProduct, AssemblyCopyright, and the GUID (use https://guidgenerator.com/)
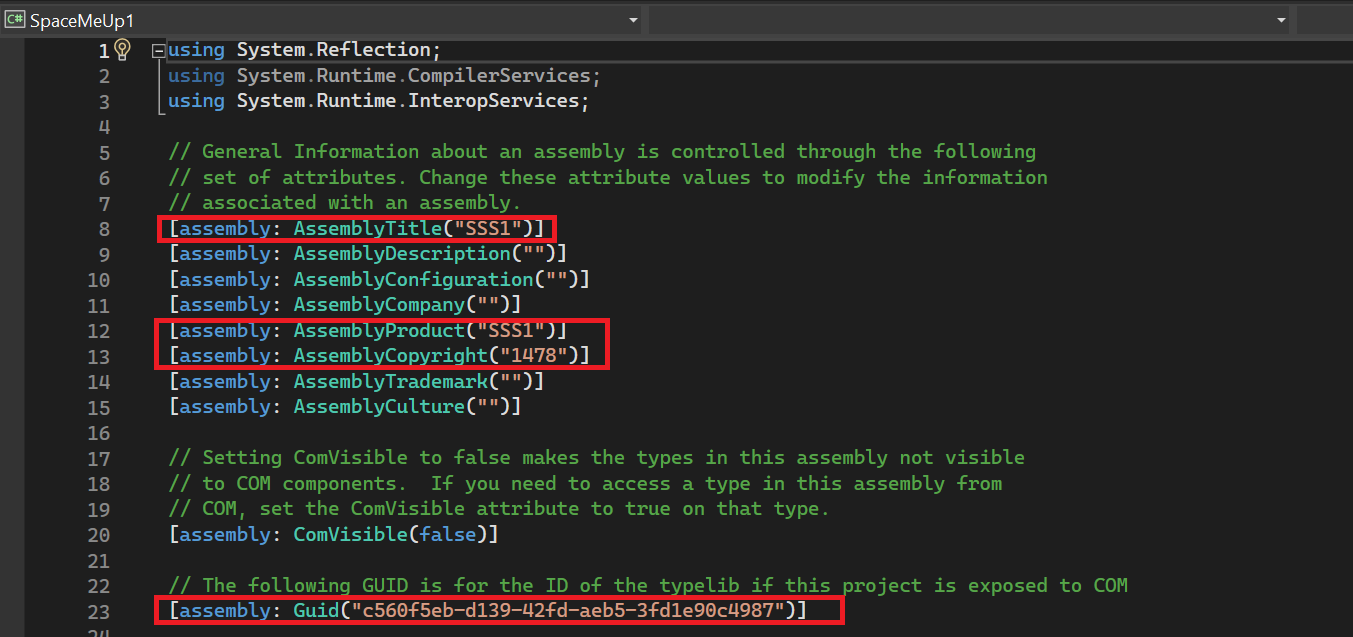
5. After changing the above-suggested options then, rebuild the program.
You should see that the name and its original descriptions have all been updated.
Conclusion
We have released SuperSharpShares to help IT engineers and security professionals enumerate shares accessible with associated domain accounts. The tool offers a swift and straightforward solution to help review internal network shares.
Insecure storage and oversharing of sensitive business data are widespread occurrences noted during security assessments; using tools such as SuperSharpShares allows internal and external professionals to identify the foundations of such dangers.
You can download and compile the tool from our git here: https://github.com/LaresLLC/SuperSharpShares

