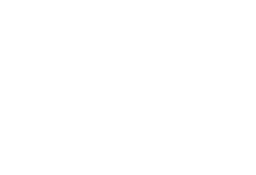From Threat to Test: Emulating Scattered Spider in Realistic Scenarios

At Lares, we specialize in threat simulation and adversarial collaboration with our clients, replicating the tactics, techniques, and procedures (TTPs) observed in the latest cybercriminal groups. By studying real-world incidents, like those perpetrated by Scattered Spider, we design controlled simulations to test organizational defenses, evaluate incident response readiness, and identify gaps across networks, endpoints, and cloud environments.
Our approach combines ethical hacking, red teaming, and threat emulation to provide actionable intelligence. Clients benefit from hands-on exercises that mirror the strategies of sophisticated actors, including social engineering, credential theft, and advanced persistence techniques, allowing organizations to strengthen their security posture proactively.
In this post, we provide an overview of the operations and tactics of the advanced persistent threat (APT) group Scattered Spider, highlighting their typical attack patterns and the lessons organizations can draw to strengthen defenses. Rather than a step-by-step technical breakdown, this post focuses on the overall flow of their attacks, from initial access and social engineering to lateral movement, privilege escalation, and exfiltration, offering a high-level perspective on how sophisticated threat actors operate in today’s digital landscape.
Scattered Spider
Scattered Spider is a financially motivated APT group that emerged in May 2022. Initially, they focused on telecommunications companies and business process outsourcing (BPO) firms. Over time, their attacks expanded to sectors such as hospitality, retail, healthcare, and aviation.
The group is primarily composed of young, native English-speaking individuals aged between 19 and 22, based in the United States and the United Kingdom. They are known for their sophisticated social engineering tactics, including SIM swapping, phishing, and exploiting weak verification processes to gain unauthorized access to systems.
Scattered Spider has been linked to several high-profile cyberattacks, including the breaches of MGM Resorts and Caesars Entertainment in 2023, which led to significant operational disruptions and ransom payments. The group often acts as an initial access broker, enabling ransomware affiliates to deploy attacks, and has been associated with various ransomware variants, including BlackCat/ALPHV and DragonForce.
Their technical expertise extends to cloud environments, with a deep understanding of platforms like Microsoft Azure, Google Workspace, and AWS. This technical proficiency, combined with their social engineering skills, makes Scattered Spider a formidable threat to organizations across multiple industries.
Other aliases used by the group include:
- UNC3944 – used by Mandiant
- Octo Tempest – used by Microsoft
- 0ktapus – used by Group-IB
- Muddled Libra – used by Palo Alto Networks
- Scatter Swine – used by Okta
- Star Fraud – self-attributed by the group
- Storm-0875 – used by Microsoft
- LUCR-3 – used by Permiso
Attack Timeline
The following timeline highlights notable attacks carried out by the group over recent years:

Tactics and Tools
Reconnaissance & infrastructure
Scattered Spider leverages OSINT techniques to gather information on employees and corporate targets, primarily using LinkedIn and other professional networks to map organizational structures. They also exploit publicly available data breaches and purchased private datasets, register domains similar to target companies for phishing, and use CDNs and domain fronting to obscure their infrastructure, enabling more effective social engineering and targeted attacks.
According to the latest update from CISA, the domains used follow the pattern:
- targetsname-sso[.]com
- targetsname-servicedesk[.]com
- targetsname-okta[.]com
- targetsname-cms[.]com
- targetsname-helpdesk[.]com
- oktalogin-targetcompany[.]com
Initial Access
The group used open-source platforms to gather intelligence on potential targets. They also acquired employee or contractor credentials from cybercriminal marketplaces and exploited third-party services with network access.
Scattered Spider employs multiple social engineering techniques to compromise targets, including smishing, vishing, and phishing, often convincing victims to install legitimate remote access management tools. Other tactics include:
Bypassing multi-factor authentication (MFA): Using push bombing, social engineering, or SIM swaps to circumvent additional verification steps:
- Push bombing: Flooding a user with repeated MFA push notifications until one is approved, bypassing MFA.
- SIM swap attacks: Convincing mobile carriers to transfer a victim’s phone number to a SIM controlled by the attacker, allowing access to calls, texts, and MFA codes.
Installing remote access tools (RATs): Deploying software that gives attackers remote control over devices or networks for surveillance, data theft, or further compromise.
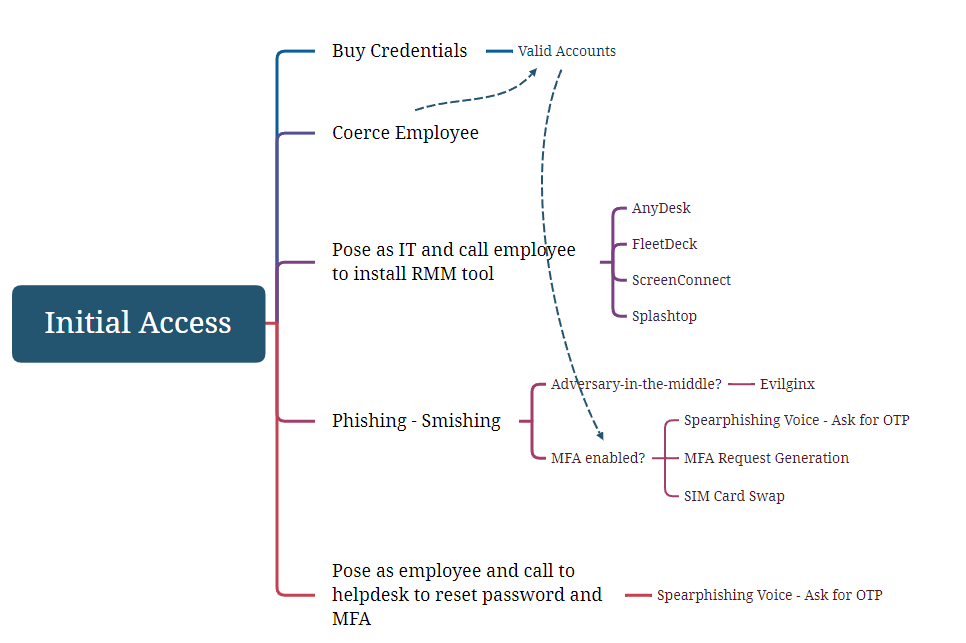
Privilege Escalation
Scattered Spider leverages a wide range of privilege escalation techniques to expand their access within victim environments. These include cloud credential theft using tools like aws console or MicroBurst to compromise cloud secrets.
To achieve privilege escalation on Windows machines, the group used advanced tactics such as and Bring Your Own Vulnerable Driver (BYOVD) attacks exploiting signed but vulnerable Microsoft drivers. They also harvest sensitive secrets via tools such as Jetcretz and GitGuardian, and exploit common Active Directory weaknesses like ADCS (Active Directory Certificate Services) abuse, reading LAPS passwords, or performing credential dumping of LSASS memory and NTDS.dit using secretsdump or Mimikatz.
Another common technique used by the group for privilege escalation is the abuse of misconfigurations in privilege relationships between Active Directory objects. They exploited improperly configured Discretionary Access Control Lists (DACLs) to gain elevated permissions, enabling actions such as modifying critical security settings or adding accounts to privileged groups.

Additionally, the group abuses Single Sign-On (SSO) sessions on workstations to gain access to sensitive internal resources such as SharePoint, and Slack:
Defense evasion
The APT group uses BYOVD (Bring Your Own Vulnerable Driver) techniques, deploying a custom loader called STONESTOP to load a Microsoft-signed but vulnerable driver, POORTRY, in user space. This approach allows them to terminate EDR or antivirus agent processes.
By abusing a Microsoft-signed vulnerable driver, they bypass signature checks and disable security defenses, giving them the freedom to operate quietly during critical stages such as data theft or ransomware deployment. In addition, they used software signing certificates stolen from the compromised internal certification authorities of victim organizations to sign their malicious binaries.
To avoid detection related to lateral movement, Scattered Spider create instances in the cloud to use during lateral movement and data collection.
Credential Access
During the reported attack chains, Scattered Spider leveraged common credential-harvesting techniques, including LSASS dumping through Sysinternals tools such as ProcDump or well-known utilities like Mimikatz. They also employed LAPSToolkit to obtain clear-text LAPS credentials by abusing accounts with permissions to read them. Once the environment was compromised, the group used the Domain Controller Active Directory replication (DCSync) to further their access and extract NTDS.dit.
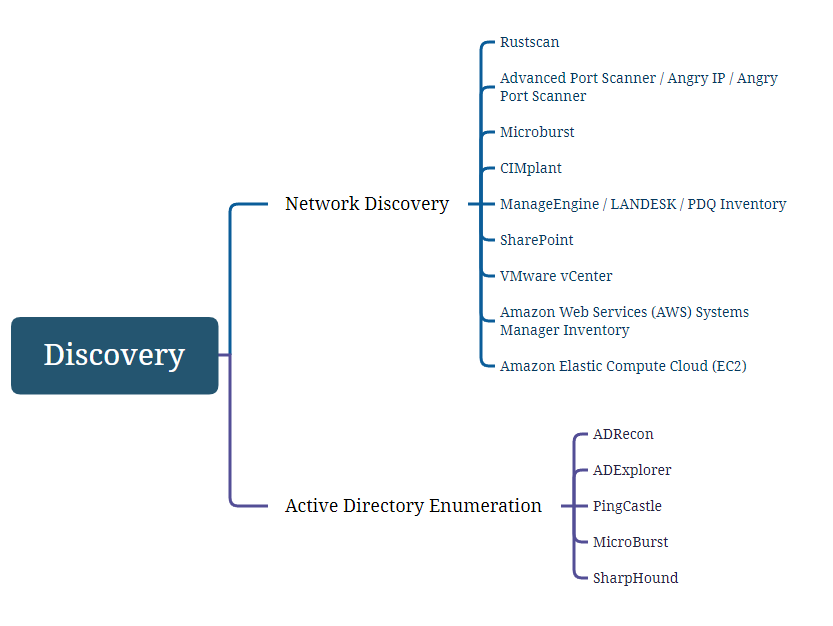
Discovery
During the Network Discovery phase, Scattered Spider prioritizes techniques that leverage both scanning tools and internal resources within the compromised environment.
They use common port and service scanning utilities such as RushScan or Advanced Port Scanner to map the network infrastructure and identify active systems and services. Simultaneously, they explore internal resources, including SharePoint, to locate documentation on network architecture, diagrams, and other sensitive information that could facilitate subsequent operations.
The group also utilizes Microburst, which includes functions and scripts that support Azure Services discovery, weak configuration auditing.
Other common tools such as ManageEngine, and Amazon Web Services inventory, always aiming, whenever possible, to use legitimate tools native to the target environment to reduce detection by security solutions and maintain a low-profile attack.
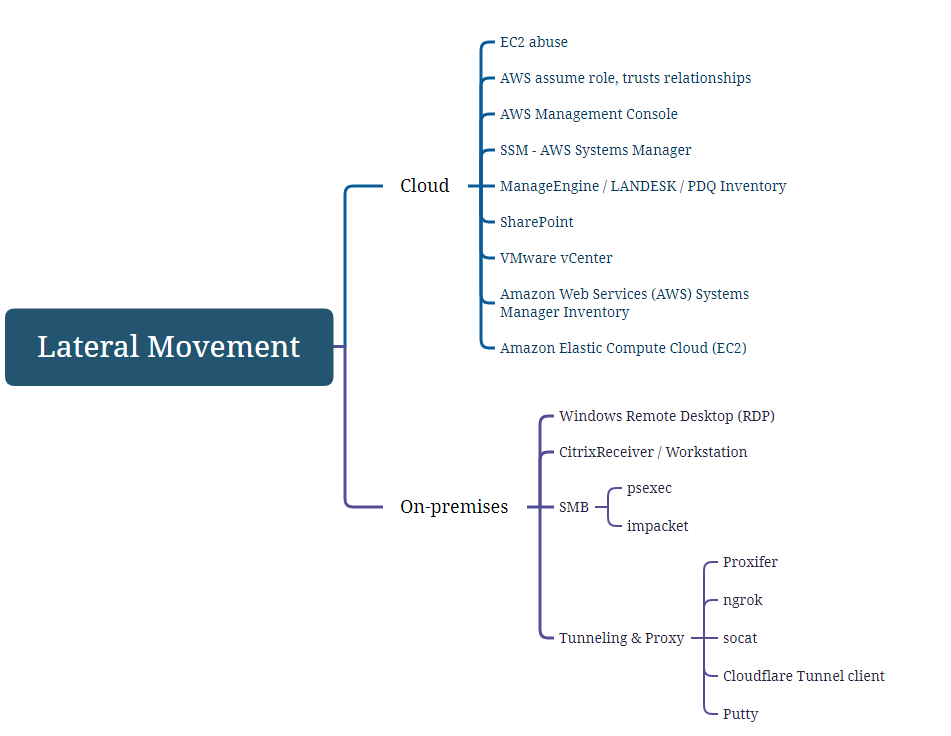
Lateral Movement
Regarding lateral movement, Scattered Spider consistently prioritized the use of native techniques within the compromised environment to reduce detection risk. This included leveraging Single Sign-On (SSO) sessions from compromised workstations to access additional internal resources via RDP or Chrome Remote Desktop.
The group made use of Proxifier, a tool that enables the redirection of internal traffic through attacker-controlled systems, allowing them to execute malicious tools without triggering Endpoint Detection and Response (EDR) or antivirus solutions.
In the cloud side, the group exploited Amazon EC2 instances and the AWS Management Console to take advantage of asume role, group and policies misconfigurations. By abusing overly permissive Identity and Access Management (IAM) policies, Scattered Spider was able to pivot laterally between instances and compromise additional user accounts, expanding their control across the victim’s cloud infrastructure.
Exfiltration
Scattered Spider employed multiple exfiltration methods to ensure the successful extraction of compromised data while minimizing detection.
For smaller, high-value files, the group leveraged Telegram, using its encrypted messaging capabilities to transmit data securely.
To handle large-scale data transfers, they utilized Rclone to move substantial volumes to attacker-controlled cloud infrastructure, and MEGAsync to synchronize stolen files directly to cloud storage accounts. Additionally, Storage Explorer was deployed to extract sensitive information from both cloud storage repositories and enterprise databases, enabling the actors to target a broad range of valuable assets across the victim environment.
Conclusion
The operations of Scattered Spider illustrate a reality that modern organizations cannot ignore: adversaries blend technical proficiency with human-focused deception to bypass even the most advanced defenses. Their reliance on social engineering, abuse of cloud misconfigurations, and creative privilege escalation highlights how security gaps extend beyond technology into processes and people. Their targets, spanning telecommunications, hospitality, healthcare, retail, and aviation, reflect a strategy aimed at industries where service disruption or data loss translates directly into financial leverage.
At Lares, our mission is not only to document these tactics but to bring them to life in controlled environments where our clients can confront them head-on. By emulating real-world adversaries like Scattered Spider, we help organizations test resilience, validate detection capabilities, and train teams to recognize and contain attacks before they escalate. Our objective is clear: to shift organizations from reactive to proactive, ensuring they are not merely aware of threats, but prepared to withstand and outmaneuver them.
Techniques
Reconnaissance & infrastructure
| Technique (ID) | MITRE ATT&CK Name | Description | Category |
|---|---|---|---|
| T1592 | Gather Victim Host Information | Collecting information about victim hosts, such as operating systems, configurations, and installed software. | Reconnaissance |
| T1595 | Active Scanning | Actively scanning the victim’s infrastructure to identify live systems, exposed services, and potential vulnerabilities. | Reconnaissance |
| T1596 | Search Open Technical Databases | Searching open technical databases to obtain information about the victim, such as WHOIS records, SSL/TLS certificates, and network scanning data. | Reconnaissance |
| T1588 | Obtain Capabilities | Acquiring capabilities that can be used during the reconnaissance phase, including malware, exploits, and commercial tools. | Resource Development |
| T1593 | Search Open Websites/Domains | Searching websites and open domains to gather information about the victim, including business relationships, physical locations, and organizational roles. | Reconnaissance |
Initial Access
| Technique (ID) | MITRE ATT&CK Name | Description | Category |
|---|---|---|---|
| T1586 | Compromise Accounts | Acquiring credentials from cybercriminal marketplaces or other illicit sources. | Credential Access |
| T1111 | Multi-Factor Authentication Interception | Intercepting or bypassing multi-factor authentication mechanisms. | Credential Access |
| T1556.006 | Modify Authentication Process | Modifying the authentication process to bypass or disable MFA (e.g., push bombing, social engineering). | Credential Access |
| T1451 | SIM Card Swap | Gaining access to mobile devices by transferring a victim’s phone number to a SIM controlled by the attacker. | Credential Access |
| T1071 | Application Layer Protocol | Using application layer protocols for command and control communications, often for RAT deployment. | Command and Control |
| T1566 | Phishing | Techniques involving sending fraudulent communications (email, SMS, social media) to trick users into revealing credentials or installing malware. | Initial Access / Social Engineering |
Privilege Escalation
| Technique (ID) | MITRE ATT&CK Name | Description | Category |
|---|---|---|---|
| T1078 | Valid Accounts | Using stolen or compromised credentials—including cloud credentials obtained via tools like aws_console or MicroBurst—to escalate privileges across environments. | Privilege Escalation |
| T1215 | Kernel Modules and Extensions (BYOVD) | Leveraging Bring Your Own Vulnerable Driver (BYOVD) attacks: loading signed but vulnerable Microsoft drivers to disable EDR/AV and elevate privileges. | Privilege Escalation / Defense Evasion |
| T1552.001 | Unsecured Credentials: Cloud Storage | Harvesting credentials and secrets from services such as Jetcretz and GitGuardian to gain sensitive information and escalate access. | Credential Access / Privilege Escalation |
| T1552.002 | Unsecured Credentials: Credentials in Files | Extracting secrets from configuration files or code repositories using tools like Jetcretz and GitGuardian. | Credential Access / Privilege Escalation |
| T1552.003 | Unsecured Credentials: Credentials In Registry | Locating credentials stored insecurely in the registry to gain elevated privileges. | Credential Access / Privilege Escalation |
| T1552.004 | Unsecured Credentials: Credentials In Cloud | Accessing credentials stored in cloud metadata or inventory services (e.g. AWS inventory) to gain higher-level access. | Credential Access / Privilege Escalation |
| T1555.003 | Credentials from Local Systems: LAPS | Reading Local Administrator Password Solution (LAPS) credentials to elevate privileges within Active Directory environments. | Credential Access / Privilege Escalation |
| T1003 | OS Credential Dumping | Dumping LSASS memory or NTDS.dit using tools like Mimikatz or secretsdump to obtain password hashes. | Credential Access / Privilege Escalation |
| T1556 | Modify Authentication Process | Abusing Single Sign-On sessions on workstations to escalate privileges and access internal resources like SharePoint or Slack. | Privilege Escalation |
Defense evasion
| Technique (ID) | MITRE ATT&CK Name | Description | Category |
|---|---|---|---|
| T1215 | Kernel Modules and Extensions | Loading vulnerable or malicious drivers in the kernel or user space to bypass security controls. | Defense Evasion |
| T1218.002 | Signed Binary Proxy Execution: Compiled HTML File | Using signed or trusted binaries or drivers to execute malicious code and bypass security solutions. | Defense Evasion |
| T1215 | Bring Your Own Vulnerable Driver (BYOVD) | Deploying custom loaders and vulnerable signed drivers to disable security software and evade detection. | Defense Evasion |
| T1570 | Cloud Instance Metadata API | Using cloud instances or APIs for reconnaissance, lateral movement, or data collection while avoiding local detection. | Lateral Movement / Reconnaissance |
| T1560 | Archive Collected Data | Collecting and compressing data in the cloud to exfiltrate or stage later without touching the compromised endpoints. | Exfiltration / Data Staging |
Credential Access
| Technique (ID) | MITRE ATT&CK Name | Description | Category |
|---|---|---|---|
| T1003 | OS Credential Dumping | Dumping credentials from the operating system, including LSASS memory, using tools like Mimikatz or ProcDump. | Credential Access |
| T1555.003 | Credentials from Local Systems: LAPS | Abusing accounts with permissions to read LAPS (Local Administrator Password Solution) credentials to obtain clear-text passwords. | Credential Access |
| T1008 | DCSync | Abusing the Domain Controller replication feature to extract password hashes and account data from Active Directory. | Credential Access |
Discovery
| Technique (ID) | MITRE ATT&CK Name | Description | Category |
|---|---|---|---|
| T1595 | Active Scanning | Scanning the network to identify active systems, open ports, and available services using tools such as RushScan or Advanced Port Scanner. | Reconnaissance |
| T1592 | Gather Victim Network Information | Collecting information about network architecture, internal servers, and services, including using SharePoint to find documentation. | Reconnaissance |
| T1614 | Internal Network Discovery | Using legitimate management platforms such as Microburst, ManageEngine, and AWS Inventory to explore and map internal networks. | Reconnaissance |
Lateral Movement
| Technique (ID) | MITRE ATT&CK Name | Description | Category |
|---|---|---|---|
| T1021 | Remote Services | Use of compromised SSO sessions to access internal resources via RDP or Chrome Remote Desktop. | Lateral Movement |
| T1090 | Proxy | Redirecting internal traffic through attacker-controlled systems to run malicious tools without detection. | Lateral Movement |
| T1078 | Valid Accounts | Using valid credentials obtained from compromised SSO sessions to access other systems and maintain persistence. | Defense Evasion / Lateral Movement |
| T1078 | Valid Accounts (Cloud IAM Abuse) | Abusing overly permissive IAM policies in AWS to pivot between instances and compromise additional accounts, expanding control in the cloud. | Lateral Movement / Cloud |
Exfiltration
| Technique (ID) | MITRE ATT&CK Name | Description | Category |
|---|---|---|---|
| T1074 | Data Staged | Scattered Spider stages data in a centralized database prior to exfiltration. | Exfiltration |
| T1567.002 | Exfiltration to Cloud Storage: Web Service | Scattered Spider exfiltrates victim data to the MEGA file sharing site. | Exfiltration |
| T1530 | Data from Cloud Storage | Scattered Spider extracts data from cloud storage services. | Exfiltration |
Resources
- CISA - Scattered Spider
- MITRE - Groups : Scattered Spider
- Splunk - Scattered Spider Isn’t a Glitch, It’s a Warning
- CybersecurityDive - What we know about the cybercrime group Scattered Spider
- American Hospital Association - Tactics by Scattered Spider cybercriminals highlighted in joint advisory